
Table of Contents
Payload Creation

Msfvenom Tutorials for Beginners
Hello friends!! Today we will learn to create payloads from a popular tool known as Metasploit, we will explore various option available within the tool to create payloads with different extensions and techniques. Msfvenom Msfvenom is a command line instance of Metasploit that is used to generate an…
Creating Metasploit Payloads
Often one of the most useful (and to the beginner underrated) abilities of Metasploit is the msfpayload module. Multiple payloads can be created with this module and it helps something that can give you a shell in almost any situation. For each of these payloads you can go into msfconsole and select…
File Transfer & File Upload

Post Exploitation File Transfers on Windows the Manual Way
Post exploitation techniques for file transfers on Windows operating systems without the use of Metasploit or other advanced tools.

Bypassing File Upload Restrictions
File upload functionality in web applications can unveil a large amount of information to a potential attacker or in certain occasions can lead to full system compromise.In this article we saw how …
Enumeration

Network Scanning using NMAP (Beginner Guide)
Nmap (“Network Mapper”) is a free and open source (license) utility for network discovery and security auditing. Many systems and network administrators also find it useful for tasks such as network inventory, managing service upgrade schedules, and monitoring host or service uptime. Nmap uses raw I…
WEB

Comprehensive Guide on Gobuster Tool
Hello Friend!! Today we are going demonstrate URLs and DNS brute force attack for extracting Directories and files from inside URLs and sub-domains from DNS by using “Gobuster-tool”. Table of Content Introduction & Installation Using Wordlist for Directory Brute-Force Obtaining Full Path for a direc…
SMB

NetBIOS and SMB Penetration Testing on Windows
From Wikipedia NetBIOS (Network Basic Input/Output System) NetBIOS is a service which allows communication between applications such as a printer or other computer in Ethernet or token ring network via NetBIOS name. NetBIOS name is 16 digits long character assign to a computer in the workgroup by WI…

A Little Guide to SMB Enumeration
Enumeration is a very essential phase of Penetration testing, because when a pentester established an active connection with the victim, then he tries to retrieve as much as possible information of victim’s machine, which could be useful to exploit further. In this article, we had explored SMB enume…
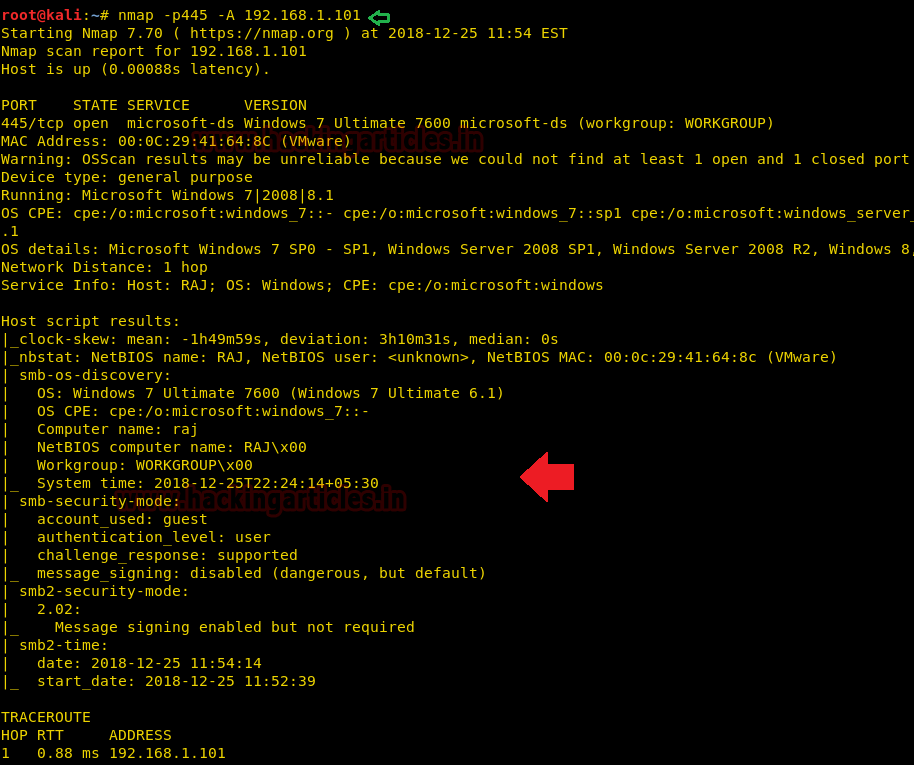
SMB Penetration Testing (Port 445)
In this article, we will learn how to gain control over our victim’s PC through SMB Port. There are various ways to do it and let take time and learn all those because different circumstances call for a different measure. Table of Content Introduction to SMB Protocol Working of SMB Versions of Windo…
Search Exploit

Comprehensive Guide on SearchSploit
Hello friends!! Several times you might have read our articles on CTF challenges and other, where we have used searchsploit to find out an exploit if available in its Database. Today in this article we are going to discuss searchsploit in detail. Table of Content Introduction to searchsploit Title S…
Reverse Shell
Reverse Shell Cheat Sheet | pentestmonkey
If you’re lucky enough to find a command execution vulnerability during a penetration test, pretty soon afterwards you’ll probably want an interactive shell.
pentestmonkey/php-reverse-shell
Contribute to pentestmonkey/php-reverse-shell development by creating an account on GitHub.
Bruteforce
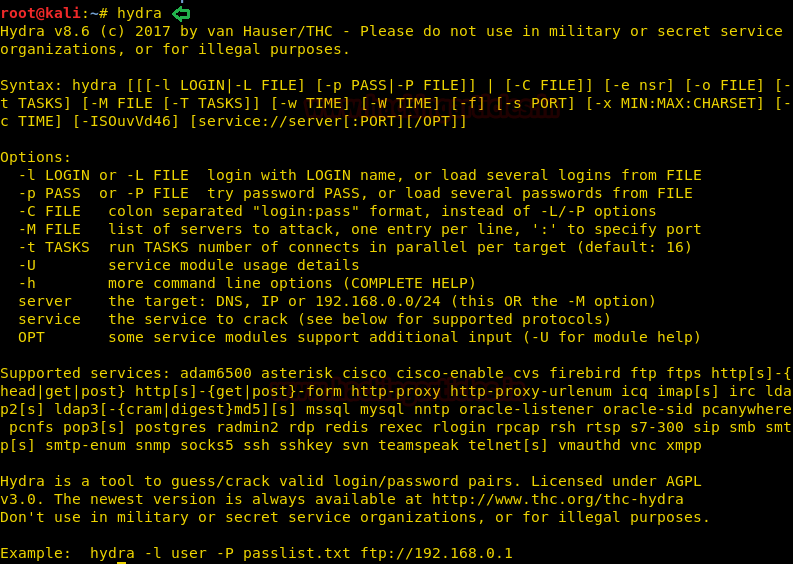
Comprehensive Guide on Hydra – A Brute Forcing Tool
Hello friends!! Today we are going to discuss – How much impactful hydra is in cracking login credentials of various protocols to make unauthorized access to a system remotely. In this article, we have discussed each option available in hydra to make brute force attacks in the various scenario. Tab…
Hash Analysis
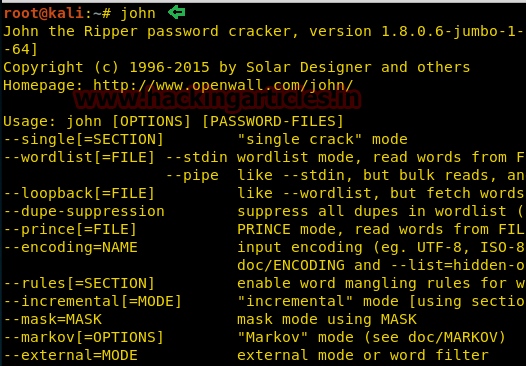
Beginners Guide for John the Ripper (Part 1)
We know the importance of John the ripper in penetration testing, as it is quite popular among password cracking tool. In this article, we are introducing John the ripper and its various usage for beginners. What is John the Ripper? John the Ripper is a free password cracking software tool developed…
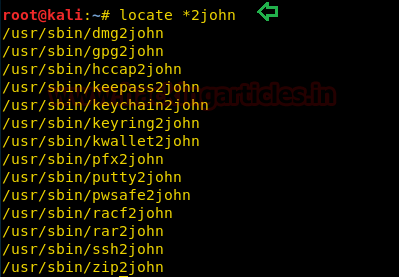
Beginners Guide for John the Ripper (Part 2)
We learned most of the basic information on John the Ripper in our Previous Article which can be found here. In this article, we will use John the Ripper to crack the password hashes of some of the file formats like zip, rar, pdf and much more. To crack these password hashes, we are going… Continu…
Upgrade Shell
Spawning a TTY Shell
Often during pen tests you may obtain a shell without having tty, yet wish to interact further with the system. Here are some commands which will allow you to spawn a tty shell. Obviously some of this will depend on the system environment and installed packages.
Privilege Escalation
Linux

Basic Linux Privilege Escalation
Before starting, I would like to point out – I’m no expert. As far as I know, there isn’t a

Linux Privilege Escalation using Sudo Rights
In our previous articles, we have discussed Linux Privilege Escalation using SUID Binaries and /etc/passwd file and today we are posting another method of “Linux privilege Escalation using Sudoers file”. While solving CTF challenges, for privilege escalation we always check root permissions for any …
Linux Privilege Escalation using SUID Binaries
In our previous article we have discussed “Privilege Escalation in Linux using etc/passwd file” and today we will learn “Privilege Escalation in Linux using SUID Permission.” While solving CTF challenges we always check suid permissions for any file or command for privilege escalation. It is very im…

Escape From SHELLcatraz – Breaking Out of Restricted Unix Shells
Presentation on breaking out of restricted Unix shells (such as rbash or rksh). SecTalks Melbourne 0x01 2016 References:
https://pen-testing.sans.org/blog/pen-testing/2012/06/06/escaping-restricted-linux-shells http://pentestmonkey.net/blog/rbash-scp…
https://pen-testing.sans.org/blog/pen-testing/2012/06/06/escaping-restricted-linux-shells http://pentestmonkey.net/blog/rbash-scp…
Windows
Windows Privilege Escalation Guide
Privilege escalation always comes down to proper enumeration. But to accomplish proper enumeration you need to know what to check and look for. This takes familiarity with systems that normally comes along with experience. At first privilege escalation can seem like a daunting task, but after a whil…
Port Forwading
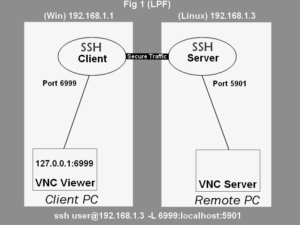
SSH Local and Remote Port Forwarding with VNC
How local port forwarding and remote port forwarding are used for tunneling VNC over SSH
Pentesting Cheatsheet

Red Teaming Experiments
nmap 10.1.1.1 –open -oG scan-results; cat scan-results | grep ”/open” | cut -d ” ” -f 2 > exposed-services-ips

